J. Cent. South Univ. (2017) 24: 2314-2321
DOI: https://doi.org/10.1007/s11771-017-3643-1
Phase type delay distribution with PU return and sensing error in CR networks
Mohammad Reza Amini, Hemati Farzad
Department of Electrical Engineering, College of Engineering,Borujerd Branch, Islamic Azad University, Borujerd, Iran
 Central South University Press and Springer-Verlag Berlin Heidelberg 2017
Central South University Press and Springer-Verlag Berlin Heidelberg 2017
Abstract:
Many studies have been done in cognitive radios to maximize the network efficiency. There is always a trade-off between sensing and transmission time which has been addressed fully in the literature. There is also some missed idle times during the waiting phase when secondary user finds the channel busy. Therefore, the longer the transmission time is, the higher the successfully delivered bits would be and the higher the missed idle times in the waiting stage would be expected. In this work, we formulate these missed idle times to addressed this trade-off. Furthermore, interference due to PU re-occupancy is modelled in successful transmitted time and in collision probability. Moreover, we derive secondary user’s packet delay distribution using phase type model at which retransmission due to collision results from both sensing error and PU re-occupancy is considered. Thanks to derived delay distribution, any statistical moments of delay could be found as a closed form mathematical expression. These moments can be used as constraints for applications with delay sensitive packets. Numerical results are given to clarify the network metrics. Finally, the optimized values for sensing and transmission time are computed using genetic algorithm in order to maximize access efficiency.
Key words:
phase type distribution; spectrum sensing; cognitive radio; access efficiency;
1 Introduction
CRNs were proposed to solve the paradox between spectrum scarcity and spectrum underutilization. These networks present dynamic spectrum access strategy (DSA) instead of fixed spectrum access (FSA) [1-3]. Furthermore, some application specific systems such as command and payload signals for unmanned aerial vehicles, vehicular radars for improved safety on the roads and many others are on the way but it is not cost efficient for them to allocate fixed spectrum band [4]. In the latest studies, the notion of successful transmitted time (or equivalently successful transmitted bits or Good-bit) is considered a network metric [5-8]. It is defined as the difference of transmission time and interference time between the secondary user (SU) and the primary user (PU). There are two kinds of interference between PU and SU. One is the interference due to sensing error, which is characterized by miss-detection probability, and the other is the interference due to PU re-occupancy which occurs during the SU transmission time and does not depend on sensing strategy. The former depends on the ROC curve of the sensor (sensing accuracy) and the latter depends on the PU traffic behaviour. A few studies such as Refs. [9, 10] pay attention to both kinds of interferences in defining network efficiency or formulating network metrics like collision probability, yet no study considers the idle times when the SU is waiting for the next sensing phase to come. We call these idle times missed opportunities. These idle times become important when the PU traffic ranks as dynamic and highly dynamic (fast changing). It is always said that in DSA, there is an inherent trade-off between sensing time and transmission time [10-17]. While a longer sensing duration leads to a higher sensing accuracy and causes less interference, the secondary user spends less time for transmission and consumes more energy for sensing the spectrum. Conversely, when the transmission duration increases, SU has more opportunities to access the channel. Regarding to the mentioned notes, we can see that there is another inherent trade-off in the transmission phase itself because when the channel is sensed idle, in the transmission period, the SU starts sending data, but if the channel is sensed busy, the SU has to wait for another period in order for the next sensing phase to come. In this waiting phase, some idle times exists. The longer the waiting phase is the higher the missed idle times are. Therefore, it is important to consider this trade-off as well. Furthermore, to the best of our knowledge, no study considers packet delay of a secondary user due to both kinds of interferences. Nota that if PU returns to the spectrum during SU transmitting, SU’s packet should be retransmitted, hence, incur a delay. This delay is very important for applications with delay sensitive packets [18, 19].
The main contributions of this paper are to define and formulate trade-off of sensing time, transmission time, missed idle times under collision probability and packet delay for systems with dynamic spectrum access strategies considering PU re-occupancy. Furthermore, missed idle times are the other metrics for which we derive analytical equations (closed form). We formulate the delay distribution based on discrete phase type model in which not only can the average delay be derived, but also higher order moments such as delay variance could be extracted as a closed form expressions.
2 Network architecture
We consider a typical Interweave CR system in which whenever a single SU has a packet to send, it monitors a channel under opportunistic spectrum access protocol. If the SU finds the channel idle, it will start to transmit data for Ttr; otherwise, it will wait for the next frame. The frame structure is shown in Fig. 1. The sensing and transmission times are denoted as ts and Ttr. Note that the sensor’s imperfect behaviour is modelled by the two common probabilities of Pfa and Pmd. It is also assumed that the PU traffic behaviour follows a two-state continuous time Markov chain (CTMC) with exponentially distributed sojourn time in OFF and ON states with rates λoff and λon, respectively. Hence, the ON(OFF) durations are random variables denoted by Ton (Toff) which are exponentially distributed with parameters λoff(λon). Hence, the stationary probability of ON(OFF) states can be easily found as 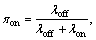
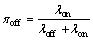 [19].
[19].
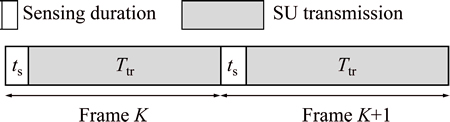
Fig. 1 Secondary user frame structure
3 Main problem and deriving corresponding metrics
The main problem is defined in here as follows:
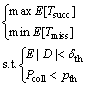 (1)
(1)
where E[·] represents the expected value; Tsucc is the successful transmission time that is the difference between total transmission time and total interference time and Tmiss is the secondary user’s missed idle time as described previously; D and Pcoll are, respectively, the packet delay and collision probability which should be kept less than some prescribed thresholds. In the following, we try to formulate the aforementioned metrics.
Based on the channel status and the sensor outcome, one of the following four scenarios will occur [9].
Case 1: Channel is idle and SU starts to send data. The percentage of time in which the channel is idle and SU correctly detects this idle state and begins to transmit data is πoff(1-Pfa). Hence, each frame can be considered Case1 frame with the mentioned probability. Then the expected value of successful transmitted time in each frame can be found as
E[Tsucc]=πoff(1-Pfa)(Ttr-I0(Ttr)) (2)
which I0(Ttr) is the expected amount of interference due to Ttr of secondary user transmission while the channel is correctly sensed idle (note that this kind of interference occurs because of PU re-occupancy).I0(Ttr) can be found in Ref. [4] as
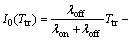
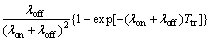 (3)
(3)
Case 2: The channel is idle and the SU false-alarms the idle state of the channel and avoids to transmitting its data. It would occur with the probability πoffPfa. So each frame can be thought as Case 2 with the mentioned probability. In this case, there are some missed opportunities (missed idle time) that should be considered. Therefore, the average missed idle of a typical frame can be derived as
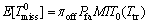 (4)
(4)
in which MIT0(Ttr) is the average amount of missed idle time due to waiting for the next sensing phase to come providing that the channel is actually idle. Note that the superscript, 0, denotes the idle state of channel. MIT0(Ttr) is derived latter in this study.
Case 3: In this case, the channel is busy and the secondary user identifies the PU presence. This case will occur with the probability πon(1-Pmd). In this case, no transmission occurs and hence the SU decides to wait for another sensing phase. There also exist some probable idle times during such a frame because the PU may vacate the channel. The average amount of this kind of missed idle time in each frame is as follows:
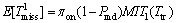 (5)
(5)
where MIT1(Ttr) is the expected amount of missed opportunities if the channel is detected busy correctly. Note that the superscript, 1, denotes the idle state of channel. This amount of missed opportunities is also formulated latter in this study. We could write in here E[Tmiss] as follows:
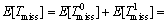
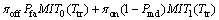 (6)
(6)
Case 4: The channel is busy and the SU miss-detects the busy state of the channel and hence starts to transmit data. In this case, a fatal interference is imposed to the PU, so this case must be avoided as much as possible. This would happen with probability of πonPmd. It means on average, each frame is of this type with the mentioned probability. The expected value of this interference time in each frame can be written as πonPmdI1(Ttr).
Which I1(Ttr) is the average amount of interference during Ttr of SU transmission if the channel is sensed idle while it is actually occupied by the PU. Although there may exist some successful transmission times during this case of frame, we are not allowed to consider these times as successful because the SU must avoid transmitting data whenever it finds the channel busy. The metric of I1(Ttr) is derived in the following.
Let us derive a formula for the metric MIT0(Ttr). The following lemma presents this metric analytically.
Theorem 1: The two metrics of missed idle times, MIT0(Ttr) and MIT1(Ttr), and the metric of interference I1(Ttr) can be mathematically derived as below.
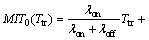
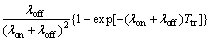 (7)
(7)
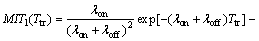
 (8)
(8)
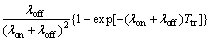
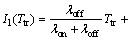
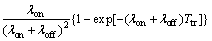 (9)
(9)
Proof: By looking at the definition of MIT0(Ttr), the following functional equation could be written.
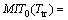
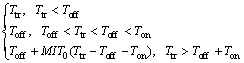 (10)
(10)
Taking expected values of both side in Eq. (10) with respect to Toff and Ton we have:
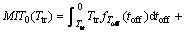

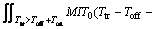
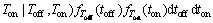 (11)
(11)
where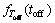 and
and 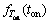 are the probability density functions of OFF/ON time in PU traffic which is considered as exponential as described in section 2. Reformulating the above equation in terms of convolution operator yields
are the probability density functions of OFF/ON time in PU traffic which is considered as exponential as described in section 2. Reformulating the above equation in terms of convolution operator yields
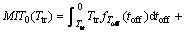

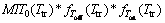 (12)
(12)
By applying Laplace transform and rearrange it, we can reach to the following final formula:
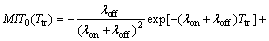
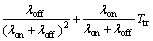 (13)
(13)
For MIT1(Ttr) and I1(Ttr) we can also write functional equations as
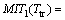
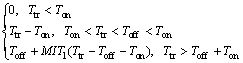 (14)
(14)
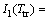
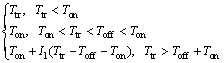 (15)
(15)
Applying the same procedure can guide us to reach following equations:
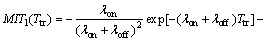
 (16)
(16)
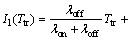
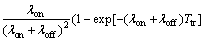 (17)
(17)
Having the extracted interference metrics, I0(Ttr) and I1(Ttr), the collision probability could be derived. Firstly, note that the expected value of interference time at each frame is given as
E[I(t)]=πoff(1-Pfa)I0(Ttr)+πonPmdI1(Ttr) (18)
Then note that by definition, collision probability can be derived based on following equation:
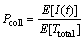 (19)
(19)
where E[Ttotal] is the expected value of total transmission time. Since transmissions occur only in Case 1 and Case 4, we can write:
E[Ttotal]=πoff(1-Pfa)Ttr+πonPmdTtr (20)
From Eqs. (18),(19) and (20), we can finally write:
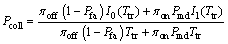 (21)
(21)
Lemma 1: Collision probability is a strictly increasing function with respect to transmission time.
Proof: See Appendix.
Lemma1 could be used in search algorithms to find the optimum values for transmission, sensing and sensor error probabilities.
Now we turn to deriving the last metric, the average packet delay. Theorem 2 gives a closed form expression for it.
Theorem 2: The average secondary user’s packet delay is shown in Eq. (22).
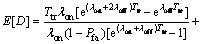
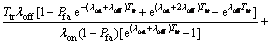 (22)
(22)
Proof: Firstly, the successive attempts of a secondary user to send a data packet successfully are modelled here by a discrete Markov Chain (Fig. 2) in which each transition corresponds to Ttr. Note that we assume three states as below.
State 1: This state shows that the channel is idle at the sensing time and the underlying packet has not been sent successfully yet.
State 2: This state indicates that at the sensing duration, the channel is busy and the underlying packet has not been transmitted successfully and it is still in the process of sending.
State 0: In this state, the packet is just successfully transmitted. Therefore, this state is the final state in the successive attempts of secondary user for sending a typical data packet and hence, it is the absorb state.
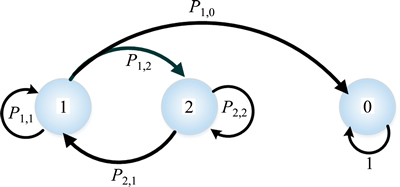
Fig. 2 Discrete Markov chain model for a packet to be delivered successfully
To draw the Markov Chain, we see the SU spectrum access process at the sensing time, each transition between states corresponds to Ttr. The total time between the packet arrival and it successful delivery is packet delay. It is equal to the amount of time from entering to the chain to absorb state. Note that when a typical packet arrives, the channel could be in idle or busy states with the stationary probability of ON(OFF) states in Section 2. If we define the initial probability matrix of entering the chain as τ=[πoff πon 0], the packet delay can be modelled as a random variable by discrete phase type distribution, PHd(τ, T), in which T is the probability transition matrix in which the absorb state is ignored. The transition probability matrix to absorb state is represented by t:
t+T1=1 (23)
where 1 denotes column vector of 1's.
If we define T as
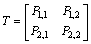 (24)
(24)
then we could easily find these transition probabilities.
In order to find some expressions for the elements of T, Pi,j i,j∈{1,2}, it is better to define some useful probabilities beforehand. First, we define pl.m as the probability that the channel goes from state l to state m within a frame time l,m∈{0,1}. l=0 corresponds to channel’s idle state and l=1 represents the channel’s busy state. Due to channel model described in Section 2, these probabilities can be found as [19]
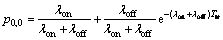 (25)
(25)
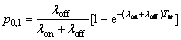 (26)
(26)
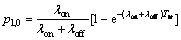 (27)
(27)
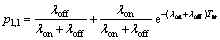 (28)
(28)
Another probability metric which should be defined is Ppr, which is the probability that the primary user returns to the spectrum during SU data transmission. It is written as follows:
Ppr=P(Toff-res<>tr) (29)
where Toff-res is the random variable represents the residual OFF time of channel. Note that the random variable Toff is exponentially distributed, thanks to memoryless property of exponential distribution, Toff-res is also exponentially distributed with the same rate as Toff. So, we have:
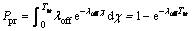 (30)
(30)
Now, we are ready to compute the elements of matrix T.
To derive P1,1, we notice that it is related to the case in which at the current frame (sensing time), the channel is idle and secondary user has a data packet to send, but in the next frame (next sensing time) the channel is also idle and the packet has not been delivered successfully. Note that if the channel is idle, a typical packet will be delivered to the SU receiver successfully unless two cases happen:
1) The secondary user false-alarms and hence, it waits for the next frame.
2) The secondary user does not false-alarm but the primary user returns to the spectrum during the SU transmission.
So, we can write:
P1,1=(1-Pfa)p0,0Ppr+Pfap0,0 (31)
For P1,2, we should consider two cases. One is when the SU false-alarms, the channel state goes from idle to busy and the other is when SU does not false-alarm but the P returns, the channel goes from idle to busy. So, we have:
P1,2=(1-Pfa)p0,1Ppr+Pfap0,1 (32)
In the same way, P2,1 corresponds to the cases in which the channel goes from busy to idle and SU either detects the PU presence and waits for the next frame or miss-detects the channel and sends its data.
P2,1=(1-Pmd)p1,0+Pmdp1,0= p1,0 (33)
P2,2 is the probability that the channel goes to stay at busy state and the SU either detects the PU presence and waits for the next frame or miss-detects the channel and sends its data.
P2,2=(1-Pmd)p1,1+Pmdp1,1= p1,1 (34)
The transition probability matrix to absorb state is as follows:
t=[P1,0 0] (35)
where P1,0 is given as:
P1,0=(1-Pfa)(1-Ppr) (36)
Note that P1,0 is related to the case at which SU does not false-alarm and PU does not return to the spectrum during SU transmission.
The expected amount of delay can be derived based on factorial moments of phase type distribution as [20]
E[D]=τ(1-T)-11×Ttr (37)
So, we could find it as Eq. (22) and the proof is now complete.
Now all the metrics in the main problem of Eq. (1) have been derived, so we can turn to find the solution in the space (Pmd, Pfa, ts, Ttr). In the next section, we pay attention to find the solution.
4 Numerical results and discussion
Some numerical results and their corresponding curves are given in this section. We used energy detector as the spectrum sensing strategy only to give insight to derived metrics. Figure 3 shows the curve of E[Tsucc] for various values of transmission and sensing times. The parameters of PU traffic are set to λon=0.2 s-1 and λoff= 0.1 s-1. As can be seen from the curve, longer sensing and transmission times lead to more successful transmission time. It is obvious that longer sensing times result in detecting the PU presence more precisely and hence less collision.
The same curve is drawn in Fig. 4 but for E[Tmiss]. Unlike E[Tsucc], as sensing and transmission times increase, the average missed idle time decreases because when the sensing time increases, the probability of false alarm decreases and hence, it helps the secondary user to find the transmission opportunities better. It is also clear that the more transmission time leads to less missed opportunities.
The collision probability is drawn in Fig. 5. As can be seen, the more the sensing time is, the more accurate the sensor acts and hence, the less interference and collision would be. On the other hand, the more transmission time leads to more interference with PU (especially interference due to PU return) and hence more collision probability will be expected.

Fig. 3 Average successful transmission time
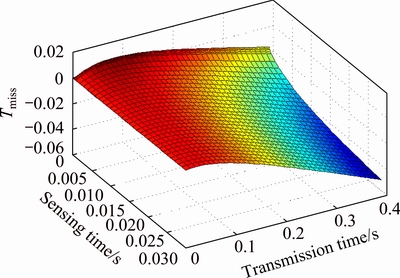
Fig. 4 Average missed idle time for different sensing and transmission time
for different sensing and transmission time
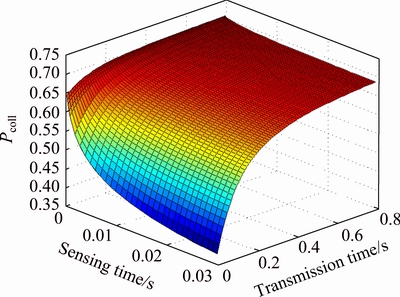
Fig. 5 Collision probability versus sensing and transmission time
Figure 6 shows average packet delay for different sensing and transmission times. It is obvious that more transmission times may lead to PU returning interference and hence results in more retransmissions and more delay. On the other hand, less sensing times will cause less accuracy and again more interference with PU and therefore, more retransmissions and more delay. So, the longer the sensing time and the shorter the transmission time, the lower the expected delay.
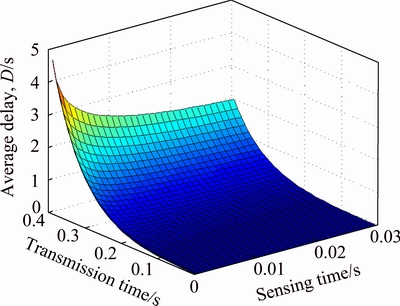
Fig. 6 Average packet delay for different sensing and transmission time
To find the solution for the problem in Eq. (1), it is better to change the max-min problem of Eq. (1) to a single min or max problem. To do this, we define a new objective function and we could write:
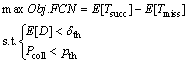 (38)
(38)
Note that sensing time itself affects both Pfa and Pmd according to ROC curve of the sensor. For example, if secondary users uses energy detector for spectrum sensing, then the relationship between probability of false alarm and miss detection and the sensing time can be approximated as [16,20]:
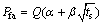 (39)
(39)
where Q(·) is the complement error function; 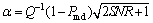 and
and 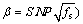 . Note that in a practical CR system, Pfa<0.5, hence, we can find the sensible range for sensing time. We can see from Eq. (14) that to find the maximum for access efficiency, four parameters of (Pmd, Pfa, ts, Ttr) should be searched under the sensor ROC constraints. We use genetic algorithm in here to find the optimum values for the mentioned four parameters. The main optimization problem is defined as follows:
. Note that in a practical CR system, Pfa<0.5, hence, we can find the sensible range for sensing time. We can see from Eq. (14) that to find the maximum for access efficiency, four parameters of (Pmd, Pfa, ts, Ttr) should be searched under the sensor ROC constraints. We use genetic algorithm in here to find the optimum values for the mentioned four parameters. The main optimization problem is defined as follows:
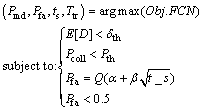 (40)
(40)
Note that the prescribed value for Pmd is imposed by primary network and usually it must be less than 0.1. We chose this value in simulation. We set Pth=0.05 and δth=100 ms. Note that the ITU G.114 specification recommends less than 150 ms one-way end-to-end delay for high-quality real-time traffic such as voice [21], so 100 ms is the sensible delay threshold. Table1 shows the genetic algorithm setting in MATLAB software.
Table 1 Genetic algorithm setting

Figure 7 shows the fitness function values for each generation of genetic algorithm. Note that the best solution (the best chromosome) achieved is (Pmd, Pfa, ts, Ttr)=(0.02, 0.9, 2.5 ms, 87 ms). It should be mentioned here that due to Eq. (38) we could omit Pfa and run the algorithm with three-gene chromosome instead of four-gene one.
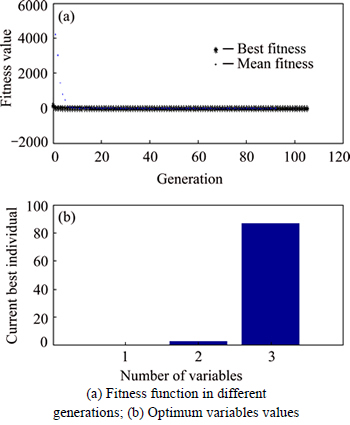
Fig. 7 Best and mean values of fitness function at each generation of genetic algorithm:
5 Conclusions
In this study, we introduced another trade-off in the wireless networks with distributed dynamic spectrum access strategy and then we formulated it. To draw a formula, the transmission time and the interference due to both sensing error and PU return are considered. We derived closed form equations for missed idle times in the waiting phase of the secondary user. We derived a distribution for packet delay of the secondary user by which any statistical moment of delay such as mean and variance can be found as closed form mathematical expressions. To do that, we used discrete phase type model. Finally, numerical results were given to clarify the dependency of different metrics on PU traffic parameters as well as SU sensor characteristics and transmission time. This dependency becomes more important when the PU traffic is ranked as dynamic or highly dynamic. The concept is important in coexisting of secondary network with fast changing primary network. Moreover, to maximize the efficiency and hence, to minimize the interference and missed idle times, and to keep average delay under prescribed threshold, we used genetic algorithm to search the solution space.
Acknowledgment
This study was supported by Islamic Azad University, Boroujerd Branch, Iran. The authors would like to acknowledge staffs of university.
Appendix
To prove that Pcoll is an increasing function, we first replace Eqs. (3) and (15) into Eq.(21). Then, by taking the first derivative with respect to Ttr we have:
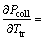
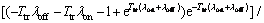
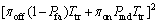 ×
×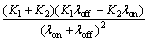
where K1=πoff(1-Pfa) and K2=πonPmd. (K1+K2) and 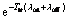 are positive expressions. Note that in a practical CR system, Pfa<0.5, then (K1λoff-K2λon) is also a positive term. To prove that Pcoll is increasing, it is sufficient to show the term (-Ttrλoff-Ttrλon-1+
are positive expressions. Note that in a practical CR system, Pfa<0.5, then (K1λoff-K2λon) is also a positive term. To prove that Pcoll is increasing, it is sufficient to show the term (-Ttrλoff-Ttrλon-1+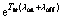 ) is positive. Because in this case,
) is positive. Because in this case, 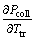 would be also positive and hence Pcoll would be increasing. To do so, we use the Taylor expansion for exponential function. Then we have:
would be also positive and hence Pcoll would be increasing. To do so, we use the Taylor expansion for exponential function. Then we have:
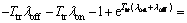
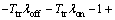
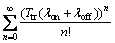
And consequently,
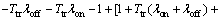
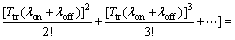
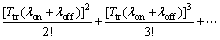
which is always a positive term when Ttr>0.
References
[1] CHATTERJEE S, MAITY S P, ACHARYA T. Energy efficiency in cooperative cognitive radio network in the presence of malicious users [J]. IEEE Systems Journal, 2016, 99: 1-10. DOI: 10.1109/ JSYST. 20162631219.
[2] MEHDAWI M, RILEY N G, AMMAR M, FANAN A, ZOLFAGHARI M. Spectrum occupancy measurements and lessons learned in the context of cognitive radio [C]//Telecommunications Forum Telfor (TELFOR). 2015: 196-199. DOI: 10.1109/telfor. 2015.7377446.
[3] SHI X Y, GE J H, LI J, ZHANG C S. Energy efficiency enhancement of two-way amplifier forward relaying with channel estimation error, [J]. Journal of Central South University, 2014, 21: 987-992. DOI: 10.1007/s11771-014-2028-y.
[4] CLEGG A, WEISSHAAR A. Future radio spectrum access [Scanning the Issue] [J]. Proceedings of the IEEE, 2014, 102: 239-241. DOI: 10.1109/JPROC.2014.2304651.
[5] ALABBASI A, REZKI Z, SHIHADA B. Energy efficient resource allocation for cognitive radios: A generalized sensing analysis [J]. Wireless Communications, IEEE Transactions on, 2015, 14: 2455-2469. DOI: 10.1109/TWC.2014.2387161.
[6] AMINI M, MIRZAVANDI A. Phase-type model spectrum sensing for cognitive radios [J]. IETE Journal of Research, 2015, 61: 1-7. DOI: 10.1080/03772063.2015.1024177.
[7] AMINI M, SAMIMI A, MIRZAVANDI A. Joint optimisation of transmission and waiting times in cognitive radio [J]. International Journal of Electronics, 2016, 103: 747-764. DOI: 10.1080/00207217.2015.1060636.
[8] AMINI M R, BALARASTAGHI E. Improving ANN BFSK demodulator performance with training data sequence sent by transmitter [C]//The Machine Learning and Computing (ICMLC), 2010 Second International Conference on. Bangalore, India, 2010. DOI: 10.1109/ICMLC.2010.28.
[9] SINGH S, SAXENA N, ROY A, KIM H. Energy efficiency in wireless networks—A composite review [J]. IETE Technical Review, 2015, 32: 84-93. DOI: 10.1080/02564602.2014.983191.
[10] AMINI M R, HEMATI F, MIRZAVANDI A. Trilateral tradeoff of sensing, transmission, and contention times in a multiuser split-phase CR networks [J]. Sensors Journal, IEEE, 2015, 15: 6044-6055. DOI: 10.1109/JSEN.2015.2453363.
[11] BHOWMICK A, ROY S D, KUNDU S. Sensing throughput trade-off for an energy efficient cognitive radio network under faded sensing and reporting channel [J]. International Journal of Communication Systems, 2015. DOI: 10.1002/dac.3087.
[12] CHE Lin, SHI Shu-yu, BIAN Kai-gui, JI Yu-sheng. Optimizing average-maximum TTR trade-off for cognitive radio rendezvous [C]//Communications (ICC), 2015 IEEE International Conference on. 2015: 7707-7712. DOI: 10.1109/ICC.2015.7249559.
[13] WANG S, WANG C. Joint optimization of spectrum and energy efficiency in cognitive radio networks [J]. Digital Communications and Networks, 2015, 1: 161-170. DOI: 10.1016/j.dcan.2015.09.004.
[14] LI Z, JIANG H, PAN Z, LIU N, YOU X. Energy spectral efficiency tradeoff in downlink OFDMA network [J]. International Journal of Communication Systems, 2015, 28: 1450-1461. DOI: 10.1002/dac.2725.
[15] LIU X, JING Q, JIA Y, ZHONG W, GUAN Y L. Sensing-throughput tradeoff for cooperative multiple-input single-output cognitive radio [J]. International Journal of Communication Systems, 2015, 28: 848-860. DOI: 10.1002/dac.2709.
[16] LIAO Y, WANG T, SONG L, HAN Z. Listen-and-talk: Full-duplex cognitive radio networks [C]//Global Communications Conference (GLOBECOM), 2014 IEEE. 2014: 3068-3073. DOI: 10.1109/GLOCOM.2014.7037276.
[17] ERRONG P E I, JIBI L I, FANG C. Sensing-throughput tradeoff for cognitive radio networks with additional primary transmission protection [J]. Journal of Computational Information Systems, 2013, 3767-3773. DOI: 10.12733/jcis4008.
[18] LIU X, ZHONG W Z, CHEN K Q. Optimization of sensing time and cooperative user allocation for OR-rule cooperative spectrum sensing in cognitive radio network [J]. Journal of Central South University, 2015, 22: 2646-2654. DOI: 10.1007/s11771-015-2795-0.
[19] ANWAR A H, SEDDIK K G, ELBATT T, ZAHRAN A H. On the effective capacity of delay constrained cognitive radio networks with relaying capability [C]//WEICHOLD M, HAMDI M, SHAKIR Z M, ABDALLAH M, KARAGIANNIDIS K G, ISMAIL M. Cognitive Radio Oriented Wireless Networks: 10th International Conference, CROWNCOM 2015. Doha, Qatar, Cham: Springer International Publishing, 2015: 767-779. DOI: 10.1007/978-3-319-24540-9_64.
[20] LATOUCHE G, RAMASWAMI V. Introduction to matrix analytic methods in stochastic modeling: Society for industrial and applied mathematics [M]. Philadelphia University City Science Center, 1987. ISBN: 978-0898714258.
[21] TIM SZIGETI C H. End-to-end QoS network design: Quality of service in LANs, WANs, and VPNs [M]. Cisco Press, 2004. ISBN: 10: 1-58705-176-1.
(Edited by YANG Hua)
Cite this article as:
Mohammad Reza Amini, Hemati Farzad. Phase type delay distribution with PU return and sensing error in CR networks [J]. Journal of Central South University, 2017, 24(10): 2314-2321.
DOI:https://dx.doi.org/https://doi.org/10.1007/s11771-017-3643-1Received date: 2016-05-12; Accepted date: 2017-03-13
Corresponding author: Hemati Farzad, Lecturer, PhD Candidate; Tel: +98-9128148541; E-mail: hemati.f@gmail.com
Abstract: Many studies have been done in cognitive radios to maximize the network efficiency. There is always a trade-off between sensing and transmission time which has been addressed fully in the literature. There is also some missed idle times during the waiting phase when secondary user finds the channel busy. Therefore, the longer the transmission time is, the higher the successfully delivered bits would be and the higher the missed idle times in the waiting stage would be expected. In this work, we formulate these missed idle times to addressed this trade-off. Furthermore, interference due to PU re-occupancy is modelled in successful transmitted time and in collision probability. Moreover, we derive secondary user’s packet delay distribution using phase type model at which retransmission due to collision results from both sensing error and PU re-occupancy is considered. Thanks to derived delay distribution, any statistical moments of delay could be found as a closed form mathematical expression. These moments can be used as constraints for applications with delay sensitive packets. Numerical results are given to clarify the network metrics. Finally, the optimized values for sensing and transmission time are computed using genetic algorithm in order to maximize access efficiency.


