J. Cent. South Univ. Technol. (2011) 18: 133-139
DOI: 10.1007/s11771-011-0670-1
![]()
Congestion aware routing algorithm for delay-disruption tolerance networks
TAO Yong(陶勇)1, 2, GONG Zheng-hu(龚正虎)2, LIN Ya-ping(林亚平)1, ZHOU Si-wang(周四望)1
1. School of Computer, National University of Defense Technology, Changsha 410073, China;
2. School of Software, Hunan University, Changsha 410082, China
? Central South University Press and Springer-Verlag Berlin Heidelberg 2011
Abstract:
There were many contradictory evaluation criteria to select next-hop in the delay-disruption tolerance networks (DTN). To solve this problem, an attribute hierarchical model was proposed, in which the predefined criteria were summarized as static identity attributes, forwarding desire attributes and delivery capability attributes (IDC). Based on this model, a novel multi-attributes congestion aware routing (MACAR) scheme with uncertain information for next-hop selection was presented, by adopting an decision theory to aggregate attributes with belief structure and computing partial ordering relations. The simulation results show that MACAR presents higher successful delivery rate, lower average delay and effectively alleviate congestion.
Key words:
delay-disruption tolerant network; congestion control; routing algorithm; custody transfer;
1 Introduction
The messages forwarding of storage-carry-forward of delay-disruption tolerance network (DTN) is different from internet’s best-effort model. The DTN routing strategy aims to the successful delivery possibility of message transmission rather than the selection of the shortest path or minimum hop counts [1]. Routing algorithm makes a routing decision according to the routing information. The deterministic routing algorithms [2-3], such as earliest delivery (ED), tree approach and space time routing, cannot apply to the scenes, in which the network topology changes randomly, because these routing algorithms need to know the global information. There are some routing schemes based on message redundancy [4-5], such as epidemic, spray and wait, spray and focus. Although these schemes adopt strategies of controlling the infection range or controlling the number of message copies to control the flooding scale, they still will cost a great of resources, which can easily cause the congestion. Some other routing schemes like PRoPHET [6], CAR [7], and HiBOp [8] are based on context like communication historical information. They are targeted to the selection of the next-hop node rather than forwarding to the neighbor node directly, which can reduce the network resource consumption. In all of these algorithms many properties of next-hop selection are proposed, such as contact probability, average time of contract, delivery probability, transmission success rate, storage utilization, space-time graph, hash index vector of a message, priority of a message, the cost to the destination node and expiration time. However, these algorithms are generally based on an assumption that network resources are unlimited. The allocation of resources is not concerned. Congestion control is the critical technology for DTN to obtain stability and acceptable reliability. In the congestion control scheme [9-14], lots of context information related to the efficiency of resources is proposed. For instance, the percentage of dropped packets, the average queue length, the package ratio of overtime retransmission, the average packet delay, the standard deviation of packet delay, congestion degree, fidelity degree, load strength and other context information. From the changes of these indicators, the degree of network congestion will change.
The selection of the next-hop node is the key issue of both the routing mechanism and the congestion mechanism. A number of evaluation criteria are proposed, which target at maximizing the possibility of data transmission or the efficiency of resource utilization. However, the current context aware systems mainly rely on the definition of scientists or users themselves. Since it is unable to deal with the conflicts among multiple attributes, the decision-maker cannot handle too much information at the same time, so, the performance of the algorithm should be further improved. BISIO et al [11] proposed a new congestion aware routing scheme in response to these deficiencies. In this scheme, each node chooses the next hop node independently based on the multi-attribute decision-making method. This algorithm puts emphases on the feasibility of application for multi-attribute decision-making. Users can choose the specific attribute and this algorithm does not involve the method for integration of different attributes.
The major contribution of this work is to implement advanced next-hop selection schemes aiming at guaranteeing high performance, through a multi-attribute optimization strategy, when facing numerous, uncertain, non-commensurable and even contradictory context information. A new congestion aware routing algorithm (MACAR) based on uncertain information was proposed.
2 IDC attribute hierarchical model
2.1 Multi-attribute decision making
Selecting the next appropriate node is just a multi- attribute (or criteria) decision-making process, and it needs to make decisions in an uncertain environment. The essence of multi-attribute decision-making is the collection of existing decision-making information (i.e. multiple attributes or criteria that are not interchangeable) and the evaluation of finite discrete solutions. We define a set C={C1, C2, …, Cm} to express the attributes of the evaluation of solutions and use the set An={a1, a2, …, aj} to represent the neighbor set of node n. The selection of next hop node of node n can be denoted as ![]() obviously
obviously ![]() as shown in Fig.1.
as shown in Fig.1.
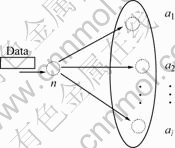
Fig.1 Selection of routing path
We can use Cj(ak) to denote the attribute value of Cj of solution ak if each attribute is a certain parameter. According to the given weight of each parameter, we can obtain the comprehensive evaluation value, C(ak), through weighted average method and finally get the best choice. However, the selection of the next hop node in DTN is a kind of mixed multi-attribute decision-making. Its criteria are related to specific strategies. So, every solution for decision-making is constrained by a number of attributes or criteria, and the value of some attributes is uncertain or difficult to obtain. The measure dimension for each attribute is generally not the same, even contrary between attributes.
The evidence theory in multi-attribute decision- making is widely used in uncertain evidence process [15] because it has many good characteristics such as denoting uncertain information easily, without prior probability and with simple reasoning form. Therefore, multiple attributes are used to assess and express their priority belief structure, then rank the schemes for replacement in priority order. In addition, we can adopt the idea of bounded rational “just cope with the situation” when we cannot obtain all the decision-making information. According to the system analysis of cost-benefit and risk-benefit, we can achieve the current “satisfactory” results and then make some gradual changes to reality, mainly including the evaluation techniques for two stages: the selection mechanism and the searching mechanism. Multi-attribute decision- making mainly consists of two parts: 1) The acquisition and processing of decision-making information; 2) The gathering and integration of acquired or processed information to make them the basis for sorting and selection.
2.2 IDC attribute hierarchical model
The acquisition and processing of decision-making information involve the selection and calculation of context, which is an attribute set that can be used to optimize message forwarding and describe the node environment. Through inductive analysis, the selection of next hop node needs to be considered comprehensively from three aspects: its own properties, the risks and benefits of receiving, and forwarding efficiency, namely, the static identity information; forwarding desire information; and transmission capacity information. We integrate them into an IDC model and then decompose it into some basic measurement parameters. Then, we establish an attribute hierarchical relationship, as depicted in Table 1.
According to the meaning of the value of each attribute parameter in DTN, we can divide them into numerical category and judgment category. The numerical category contains a beneficial-type parameter (PB), and the larger the data value of it, the superior it is. It also contains a cost-type parameter (PC), and the smaller the data value of it, the superior it is. On the other hand, judgment category contains a “right” preferred parameter (PR) and a “negative” preferred parameters (PW).
2.1.1 C1 attributes
Static identity information includes such measurement parameters as addressing, message-related information and node-related information: I= {
,1) Address: Routing relies on addressing and addressing is related to the format of address. A DTN node uses a form like (
Table 1 Attribute hierarchical model
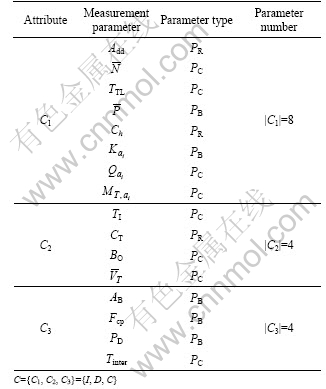
region, a DTN node prefers to send the message to the external region. Otherwise, it will send the message to the inner region first.
2) Bundle factor: It is mainly related to the survival period, size and priority of messages.
![]() is equal to bundle size/bundle average size; TTL is equal to survival time/average time and
is equal to bundle size/bundle average size; TTL is equal to survival time/average time and ![]() is equal to message priority/average priority.
is equal to message priority/average priority.
3) Node factor: Ch denotes whether it is a cluster head. Nodes can be divided into different types such as normal nodes and cluster head nodes. ![]() denotes the maximum storage space (in bytes) of a node.
denotes the maximum storage space (in bytes) of a node. ![]() denotes the current queue length of a node and
denotes the current queue length of a node and ![]() denotes the average occupancy rate of the buffer in recent time T.
denotes the average occupancy rate of the buffer in recent time T.
2.2.2 C2 attributes
In forwarding desire information the risks and benefits of data receiving are mainly considered. It includes such parameters as traffic load, transfer mode, buffer occupancy, and average risk rate: D=(<>I>, <>T>, <>O>, <![]() >).
>).
1) TI denotes traffic intensity, which represents the current and future traffic demand. Traffic intensity is equal to buffer filling rate/buffer empty rate.
2) CT denotes whether use the custody transfer mode.
3) BO is a parameter related to buffer occupancy and includes storage cost and transmission cost. Storage cost Sv(s)=![]() (s<>v), where Av expresses the free space and s represents the length of the message. If s>Av, then Sv(s) will be infinite. Transmission cost Ti(s)=lg((Li+ (s/Bi))/10-6)/10, where Li denotes the delay and Bi denotes the band width.
(s<>v), where Av expresses the free space and s represents the length of the message. If s>Av, then Sv(s) will be infinite. Transmission cost Ti(s)=lg((Li+ (s/Bi))/10-6)/10, where Li denotes the delay and Bi denotes the band width.
4) RT represents the average risk during a period of T and it is related to the size of the bundle and remainly time to live; VT represents the average profit during a period of T and it is related to the priority of the node message; and ![]() represents average risk rate and it is the ratio of RT to VT.
represents average risk rate and it is the ratio of RT to VT.
2.2.3 C3 attributes
As the DTN network connection appears occasionally, the contact occurs accidentally, and the link connect intermittently, transmission capacity information C3 mainly includes such parameters as the available band width estimated through link state, available probability of bandwidth, future contact probability between nodes and the forwarding probability: C={<>B>, <>cp>, <>D>}.
1) AB stands for available bandwidth. AB=B/|Ni|, where B denotes the total band width and |Ni| denotes the current number of receiving bundles.
2) Fcp stands for future contact probability.
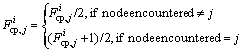
Its initial value is ![]() 1/(|s′|-1), and s′ represents a set of network nodes. Then, we can get the possibility of transmission (PLH) through PLH=Fcp/(1+Bf) which represents the frequency of node contact that will reflect the probability of a node contact with its destination node.
1/(|s′|-1), and s′ represents a set of network nodes. Then, we can get the possibility of transmission (PLH) through PLH=Fcp/(1+Bf) which represents the frequency of node contact that will reflect the probability of a node contact with its destination node.
3) The forwarding probability of node a and node b can be defined as P(a, b)=P(a, b)old+(1-P(a, b)old?Pinit), where Pinint![]() [0, 1] is an initialization constant. And the sending probability between nodes will decay over time (0<γ<1, where γ represents the decay constant), which can be denoted as P(a, b)=P(a, b)old?γk.
[0, 1] is an initialization constant. And the sending probability between nodes will decay over time (0<γ<1, where γ represents the decay constant), which can be denoted as P(a, b)=P(a, b)old?γk.
3 Description of MACAR algorithm
3.1 Priority preference relations
Relations here have three kinds, better than (>), worse than (<) and can not compare (-), namely R={r1, r2, r3}={>, <, -}. Then, the priority preference relation related to Ci (i=1, 2, 3) attribute of the next hop node ap and aq can be expressed as follows.
Definition 1: The priority preference relation with confidence level is
Ri(ap, aq)={(>, β1,i (ap, aq)), (<, β2,i(ap, aq)), (-, β3,i(ap, aq))} (1)
where βn,i(ap, aq) represents the confidence level of >, <
and - under attribute Ci. So, βn,i≥0 and ![]() Its
Its
calculation rules are as follows.
Rule 1 (Superior parameter rule): A larger beneficial-type parameter is superior to those smaller ones while a smaller cost-type parameter is superior to those larger ones. The “Right” is superior to the “Error” in the right-preferred parameters, while it is contrary among negative-preferred parameters.
Rule 2 (Inferior parameter rule): Larger ones of PB are inferior to those smaller ones while smaller ones of PC are inferior to larger ones. The “Right” is inferior to the “Error” in PR parameters while it is contrary in PW parameters.
Rule 3 (Rule of parameter with the uncertain relation): If all the values of parameters are the same or any of them is unknown, the relations among them will be uncertain.
Set g(?) as the utility function for the parameter j of attribute Ci, meeting the rules above. And set the parameters of the subset of attribute Ci as
Ja>b={j![]() Ci: gj(a)>gj(b)}, Ja
Ci: gj(a)>gj(b)}, Ja![]() Ci: gj(a)<>j(b)} and Ja-b={j
Ci: gj(a)<>j(b)} and Ja-b={j![]() Ci: gj(a)-gj(b)} represent the subsets of these three situations, respectively: a is superior to b, a is inferior to b, and the relation between a and b is uncertain. We can divide the parameters set of the attribute Ci into three parts as
Ci: gj(a)-gj(b)} represent the subsets of these three situations, respectively: a is superior to b, a is inferior to b, and the relation between a and b is uncertain. We can divide the parameters set of the attribute Ci into three parts as
![]()
![]()
![]()
They represent the number of parameters when attributes Ci meet Rule 1, Rule 2 and Rule 3, respectively. As a result, we can make use of a fuzzy rule in a format like “IF-THEN” to obtain βn,i(ap, aq): If the number of support parameters is qn,i in the total number of evaluation of |Ci|, then βn,i=qn,i/|Ci|:
![]() (2)
(2)
3.2 Uncertain attribute integration
When measuring, mixing and signifying the uncertain information, the evidence theory has a greater advantage than the Bayesian inference, the fuzzy reasoning, the probabilistic reasoning and the rule-based reasoning. The evidence theory has gone through the probability assignment, the property iterative synthesis, the combination of computing confidence and other processes. The most important is the combination rules proposed by evidence theory.
Step 1: Constructing probability assignment. Suppose that ωi represents the weights of the attributes Ci (i=1, 2, …, k), and this ωi satisfies the condition: 0
ωi≤1,![]() Use ωi to express the relative importance
Use ωi to express the relative importance
of these attributes and ψn,i=ωiβn,i(ap, aq), n=1, 2, to express the better relations and the inferior relations separately. The ψn, i is a basic probability density, which describes the extent of property Ci supporting rn, and the rn is the relation between ap and aq.
The ψR,i is surplus probability density, which describes that the extent of property Ci can not support rn. The ψR, i can be divided into two parts as
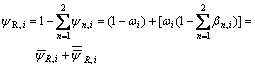
Step 2: Composite these properties iteratively. To get a combination confidence of all sub-attributes, the following algorithm composes the evidence.
Initialize:
![]()
Interate:
![]()
![]()
![]()
where ![]() represents a
represents a
normalization factor.
Step 3: Calculate the confidence level combination.
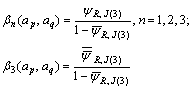
3.3 Advantages partial order
The partial order can be expressed as a directed acyclic graph, which has transitive nature. Because of these properties, the partial order can be used to represent the sequence. d(r1, r2) is used to express the degree of deviation between r1 and r2. The distance between the partial order given the calculated values of d(r1, r2) is shown in Table 2.
Table 2 Distance degree between partial orders
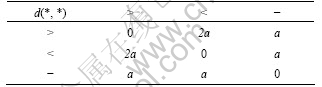
Definition 2: The priority preference relations and “<”, “>” distance weighted, respectively, are defined as d >(ap, aq) and d <(ap, aq):
![]()
![]()
Definition 3: φ>(ap) and φ<(ap) are the index numbers of the disadvantages and advantages of the node ap:
![]()
![]()
Obviously, φ>(ap) and φ<(ap) have the following properties: With the disadvantage index increasing, the distance between the > and the relations among this program and other programs is further. This means that this program is worse. From the disadvantage index (or preference index), we can know that the degree of this program is worse (or better) than the other programs.
The disadvantage index and the advantage index are utility function, can be used to measure the sorting as a support measure.
3.4 MACAR algorithm design
The routing algorithm proposed in this study uses an uncertain information inference method. It effectively merges all the congestion control-related attributes together in the selection of routing. The multi-attributes congestion aware routing algorithm is as follows.
Input: node n, attribute set C=IDC, neighbor node set An
1) Classify the selection parameter cj of the selected next hop node as IDC measurement parameters and determine its parameter type;
2) Select a neighbor node set An of node n, and use Eqs.(2)-(3) to construct a preference matrix [Ri(ap, aq)]r*3, where r is the number of neighbor nodes. Then, calculate the different priority preference relations of the solutions with a confidence level under any attribute;
3) Set the weight ωi of each IDC attribute, and use Eq.(4) and the preference matrix to obtain R(ap, aq) with a confidence structure, formatting the preference vector: R(ap, aq)={(>, β1(ap, aq)),(<, β2(ap, aq)),(-, β3(ap, aq))}
4) Construct the partial order with the low-quality index and superior index:
(1) Construct the total order V > and V < of An
V >=[]
Loop
w={ap|minφ>(as), as∈An}
V>.addElement(w)
An=An-{w}
until An is empty
And we can get the total order V< of An in the same principle.
(2) Determine the partial order R={>, <, ?} of the next hop node, using the rules as follows:
if (ap<>q for all members in V <, V > or one meets ap>aq and another meets ap-aq)
ap>aq;
if (ap>aq for all members in V <, V > or one meets ap>aq and another meets ap-aq)
ap<>q;
else
ap-aq;
5) Decision-making output DMn={k|k>a, any a∈An}, and the algorithm is over.
Compared with the single-attribute decision-making, MACAR increases the cost of computation and the number of the exchanged network information. In n alternative options, the number of multiplication and division in combining k evidence with a method of combination is the complexity of the combination method, which can be expressed by O(f(n, k)). By using the defined formula in Ref.[16] to compute the complexity, the complexity of MACAR algorithm is O(f(n, k))= O(2nk+1+k). The attribute sub-set model IDC constructed in this work, organizes a great number of metrics parameters into three top-level attributes in the way of pretreatment method. So, the expression becomes simple, and the number of dimensions is constant 3. It uses the preference matrix that is limited by the constant as the input to the integration algorithms. Thus, it effectively decreases the computational complexity and the space complexity of the integrated decision-making algorithm. In addition, if the model increases new measure parameters, it will not increase the number of top-level attributes and the computational complexity will not increase with the increase of parameters.
4 Experimental simulation
4.1 Experimental environment
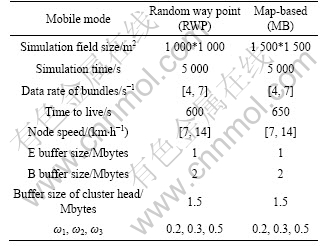
In order to analyze and evaluate the projects proposed earlier, we use the ONE simulator [17] to simulate. This open source simulator is an opportunity to network simulation environment, and it integrates mobile modeling, routing simulation, visualization and result reporting into an integrity. We rewrote the CARRouter class to support strict custody transfer algorithm. Moreover, we designed and constructed the MACARRoutes class. The network topology is shown in Fig.2. Without loss of generality, the scenarios are divided into regions 1-4, and region 3 as the backbone network includes B1-B3 transit nodes, the rest regions includes E1-E9 terminal nodes and cluster head nodes. And E1, E2, E4, E5, E6 and E9 are the source nodes, E3, E7 and E9 are the destination nodes. The link bandwidth of region 1-3 is 2 Mbit/s, region 4 is 1 Mbit/s, and the ability of link between Region 1 and Region 3, Region 2 and Region 3, Region 4 and Region 3, is 1.0, 2.0 and 0.5 Mbit/s, respectively. Table 3 gives the various values of parameters needed in the experiment.
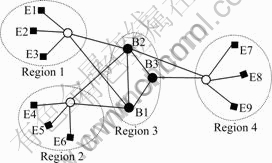
Fig.2 Simulation topology
Table 3 Experimental parameters
4.2 Experimental results
The performances of CAR and MACAR in two mobile modes of random way point (RWP) and map- based (MB) movement are simulated. The parameters of performance include four aspects: successful delivery rate, bundle dropped rate, average bundle buffer occupied ratio and average delay. The result is the statistics based on 25 independent experiments, as shown in Figs.3-6.
From Fig.3, it can be seen that with the message size increasing from 100 to 500 kbit, the changes of the successful delivery rate of the bundle are observed. As seen from Fig.2, with the MACAR algorithm we proposed, the rate of successful data transmission is better than CAR. Especially, in the case of poor network condition, the performance is improved by nearly 2.3
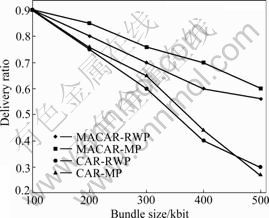
Fig.3 Successful delivery rate performance
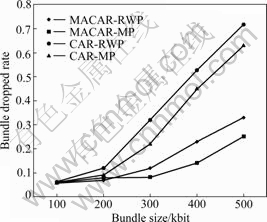
Fig.4 Bundle dropped rate performance
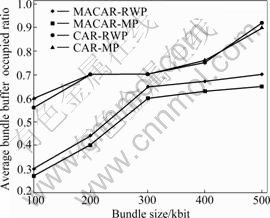
Fig.5 Average bundle buffer occupied ratio performance
times. Figs.4 and 5 show the package loss rate of the algorithm and the performance of average queue length, respectively. When the load is small, the average queue length is small and the packet loss rate is small too. However, with the increase of the load, each CAR node queue is extremely unbalanced since there is no ability to control the congestion. And it easily leads to certain key nodes to be the bottleneck; at the same time, the buffer occupancy rate increases rapidly. All these factors lead to high speed increase of packet loss rate. Fig.6 shows the
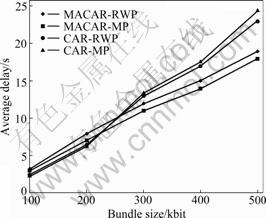
Fig.6 Average delay performance
average delay performance of message, from which we can get knowledge that the average delay of CAR is better than that of MACAR in a better network condition. However, with deteriorating the network condition, the advantage of MACAR is more obvious. What’s more, the node movement is random in the random movement pattern and does not have the regularity, so the availability of historical information is somewhat weaker. While in the MB mode, node movement follows a pattern of knowledge, so the context information guidance and the predict effect are strong.
5 Conclusions
1) A kind of congestion aware routing algorithm, MACAR, is introduced based on the multiple attribute decision making of uncertain information, in which a variety of context information from the congestion control and routing schema is considered.
2) Experimental results demonstrate that the MACAR can not only improve the successful rate of data forwarding, but also decrease the network resource consumption.
References
[1] FALL K. A delay-tolerant network architecture for challenged internets [C]// Proceedings of ACM SIGCOMM. Karlsruhe, 2003: 27-34.
[2] FALL K. HONG W, MADDEN S. Custody transfer for reliable delivery in delay tolerant networks. [EB/OL]. [2010-03-28]. http://www.dtnrg.org/papers/custody-xfer-tr.pdf.
[3] JAIN S, FALL K, PATRA R. Routing in a delay tolerant network [C]// ACM SIGCOM. Portland, 2004: 145-158.
[4] VAHDAT A, BECKER D. Epidemic routing for partially connected ad hoc networks [R]. Duke Technical Report CS-2000-06, 2000: 229-236.
[5] THRASYVOULOS S, KONSTANTINOS P, CAULIGI R. Spray and wait: An efficient routing scheme for intermittently connected mobile networks [C]// Proceedings of ACM SIGCOMM. Philadelphia, 2005: 22-26.
[6] ANDERS L, AVRI D, OLOV S. Probabilistic routing in intermittently connected networks [J]. SIGMOBILE Mobile Computing and Communication Review, 2003, 7(3): 19-20.
[7] MUSOLESI M, HAILES S, MASCOLO C. Adaptive routing for intermittently connected mobile ad hoc networks [C]// Proceedings of the 6th IEEE International Symposium on a World of Wireless, Mobile and Multimedia Networks (WoWMoM2005). Taormina- Giardini Naxos, 2005: 183-189.
[8] BOLDRINI C, CONTI M, JACOPINI J. HiBOp: A history based routing protocol for opportunistic networks [C]// IEEE International Symposium on a World of Wireless, Mobile and Multimedia Networks. Helsinki, 2007: 1-12.
[9] DE RANGO F, TROPEA M, LARATTA G B, MARANO S. Hop-by-hop local flow control over interplanetary networks based on DTN architecture [C]// IEEE ICC 2008. Beijing, 2008: 1920-1924.
[10] SCHEUERMANN B, LOCHERT C, MAUVE M. Implicit hop-by-hop congestion control in wireless multihop networks [J]. Elsevier Ad Hoc Network, 2008, 6(2): 260-286.
[11] BISIO I, DECOLA, T, MARCHESE M. Congestion aware routing strategies for DTN-based interplanetary networks [C]// IEEE GLOBECOM. New Orleans, 2008: 1-5.
[12] ZHANG Guo-hua, WANG Jing, LIU Yong-he. Congestion management in delay tolerant networks [EB/OL]. [2010-03-28] http: //portal.acm.org/citation.cfm?id=1554126.1554206
[13] BURLEIGH S, JENNINGS E, SCHOOLCRAFT J. Autonomous congestion control for an interplanetary internet [C]// AIAA SpaceOps 2006 Conference. Rome, 2006: 123-127.
[14] SELIGMAN M, FALL K, MUNDUR P. Alternative custodians for congestion control in delay tolerant networks [C]// Proceedings of SIGCOMM. Pisa, 2006: 229-236.
[15] YANG J B. XU D L. On the evidential reasoning algorithm for multiple attribute decision analysis under uncertainty [J]. IEEE Transaction Systems, Man and Cybernetics, 2002, 32(3): 289-304.
[16] HOU Jun. The evidence reasoning’s combination method, evaluation and application [D]. Xi’an: Northwestern Polytechnical University, 2006: 44-47. (in Chinese)
[17] ARI Ker?nen, J?RG Ott, TEEMU K?rkk?inen. The ONE simulator for DTN protocol evaluation [C]// SIMUTools’09: 2nd International Conference on Simulation Tools and Techniques. Rome: 2009: 243-248.
Foundation item: Project(60973127) supported by the National Natural Science Foundation of China; Project(09JJ3123) supported by the Natural Science Foundation of Hunan Province, China
Received date: 2010-09-10; Accepted date: 2010-11-29
Corresponding author: TAO Yong, PhD; Tel: +86-731-88825889; E-mail: 4889970@qq.com
- Congestion aware routing algorithm for delay-disruption tolerance networks


