CRSG: a congestion control routing algorithm for security defense based on social psychology and game theory in DTN
来源期刊:中南大学学报(英文版)2013年第2期
论文作者:WANG Cheng-jun(王珵珺) 龚正虎 陶勇 张子文 赵宝康
文章页码:440 - 450
Key words:delay/disruption tolerant networks; social psychology; game theory; congestion control; routing
Abstract: The inherent selfishness of each node for the enhancement of message successful delivery ratio and the network overall performance improvement are reflected in the contradiction relationship of competition and cooperation in delay/disruption tolerant networks (DTN). In particular, the existence of malicious node aggravates this contradiction. To resolve this contradiction, social relationship theory and group theory of social psychology were adopted to do an in-depth analysis. The concrete balancing approach which leveraged Nash equilibrium theory of game theory was proposed to resolve this contradiction in reality. Thus, a new congestion control routing algorithm for security defense based on social psychology and game theory (CRSG) was put forward. Through the experiment, this algorithm proves that it can enhance the message successful delivery ratio by more than 15% and reduce the congestion ratio over 15% as well. This algorithm balances the contradiction relationship between the two key performance targets and made all nodes exhibit strong cooperation relationship in DTN.
J. Cent. South Univ. (2013) 20: 440–450
DOI: 10.1007/s11771-013-1505-z
WANG Cheng-jun(王珵珺)1, GONG Zheng-hu(龚正虎)1, TAO Yong(陶勇)2,
ZHANG Zi-wen(张子文)1, ZHAO Bao-kang(赵宝康)1
1. School of Computer Science, National University of Defense Technology, Changsha 410073, China;
2. School of Software, Hunan University, Changsha 410082, China
 Central South University Press and Springer-Verlag Berlin Heidelberg 2013
Central South University Press and Springer-Verlag Berlin Heidelberg 2013
Abstract: The inherent selfishness of each node for the enhancement of message successful delivery ratio and the network overall performance improvement are reflected in the contradiction relationship of competition and cooperation in delay/disruption tolerant networks (DTN). In particular, the existence of malicious node aggravates this contradiction. To resolve this contradiction, social relationship theory and group theory of social psychology were adopted to do an in-depth analysis. The concrete balancing approach which leveraged Nash equilibrium theory of game theory was proposed to resolve this contradiction in reality. Thus, a new congestion control routing algorithm for security defense based on social psychology and game theory (CRSG) was put forward. Through the experiment, this algorithm proves that it can enhance the message successful delivery ratio by more than 15% and reduce the congestion ratio over 15% as well. This algorithm balances the contradiction relationship between the two key performance targets and made all nodes exhibit strong cooperation relationship in DTN.
Key words: delay/disruption tolerant networks; social psychology; game theory; congestion control; routing
1 Introduction
DTN (delay/disruption tolerant networks) [1] is widely applied in obscure or tragedy district [2], vehicle network [3], satellite communication [4] and other wireless network environment. It resolves the problem of intermittent connection, high delay, low data transfer speed, and high packet loss rate in DTN by adding a bundle layer [5] between the traditional transmission and application layer and designing the custody transfer protocol [6].
As a special wireless network environment, the chief goal of DTN is to guarantee the message successful delivery ratio. The previous algorithms mostly adopt the mechanism of increasing message replicas [7] or leverage the historical information of node’s encounter probability [8] as the criterion of transfer node selection in the message delivery.
Meanwhile, the limit of DTN resource causes the congestion which also affects the message successful delivery ratio in some extent. Previous congestion control algorithms mostly adopt the passive message delete [9] or migration [10] when congestion happens, or adjust message generation ratio and sending speed by feedback control system [11]. This kind of method usually is passive and lagging. In some extent, it results in the frequent jitter of traffic and unstable network environment.
These methods mostly assume that network nodes are normal and do not consider the presence of malicious nodes. Malicious node tends to forge the probability of its encounter with the destination node. High encounter probability is forged by malicious node (Black-hole attack) [12]. Message transfer request is accepted and then the received message is discarded. Or malicious node forges the low probability of its encounter with the destination node (Resource-misuse attack)[13] which occupies the memory of transfer node and causes network congestion. Two attack methods both block the communication between the other nodes and destination nodes and this reduces the message successful delivery ratio.
The presence of malicious nodes causes the failure of past mechanism which passively controls congestion in order to guarantee the message successful delivery ratio. The active congestion control mechanism for dealing with the attack of malicious node should be adopted. In the real DTN environment, each node represents some of the specific mobile entities, such as vehicle, ship and aircraft. These nodes are often controlled by the human beings and human psychology controls human behavior. The analysis of human psychology in social psychology [14]could be leveraged to explore new mechanisms and ideas of storage resource allocation in DTN. The actual operation of rational resource allocation should be quantified which uses the idea of game theory. Game theory [15] is importantly applied in the problem how to balance the contradictory two parties. The definite global optimal solution can be calculated through it. The ideas of social relationship and group theory in social psychology combine with the specific application of Nash equilibrium in game theory to restrain the attacks from the malicious nodes. Through balancing the rational share of network storage resource among the nodes in DTN, it can guarantee the message successful delivery ratio and effectively reduce the network congestion ratio as well.
2 Related work
To increase the message successful delivery ratio, the simplest way of leveraging message replica is flood routing [7]. The unrestricted duplication of message is a great waste of bandwidth resource. SPYROPOULOS et al [16] improved this mechanism by transferring message replicas to all neighbor nodes only in the first communication. Then, these nodes deliver message directly which decreases the amount of replicas, but the successful delivery ratio is obviously affected. SPYROPOULOS et al [17] comprehensively considered the tradeoff of resource utilization and successful delivery ratio. The message replicas were provided to successive transfer nodes with the decreasing probability until the message is delivered to the destination node at last.
The most popular message delivery strategy is the routing algorithm based on the historical information of node encounter probability [8]. This algorithm adopts custody transfer protocol and the node carries the message until it encounters the node which has larger probability to meet the destination node. This is just the primary method which malicious nodes usually take to attack other nodes in DTN. They disguise the encounter probability with the destination node to damage the normal message transfer in DTN and finally achieve the target of reducing the message successful delivery ratio.
To assign different functions for nodes, they are classified as the normal node and the ferry node. In Ref. [18], the normal node adopts random movement and the ferry node in transfer moves through a constant path to assist the normal node with message delivery. This resolves many issues in the traditional DTN. But the path selection of ferry node is still a hard problem to researchers. This motivates the idea of social network [19] applications in DTN. DTN is divided into multiple regions. The node routing mechanisms of inner-region and inter-regions are different. This application of social network chooses the routing mechanisms merely from the perspective of different community functions. But human psychology that is the most important factor of interpersonal communication has not been used to optimize the routing algorithm.
For the congestion control, the most common method in message process is to delete new arrival message or previous old message stored in the node [9]. FLOY and JACOBSON [20] added the probability management for the operation of message deleting that adopts the predefined constant threshold to control the new arrival message’s deleting ratio. SELIGMAN et al [21] introduced the migration algorithm that means when congestion happens, the message is transferred to the nearby nodes. Migration will result in the increase of message transfer overhead, the decrease of message successful delivery ratio and increase of message delivery delay. In Ref. [22], a new multi-attribute hierarchical model was proposed to avoid congestion through selecting the appropriate next-hop.
In the aspect of message sending speed adjustment, NISHIYAMA et al [23] defined the threshold to implement additive increase multiplicative decrease (AIMD) which was first proposed in Ref. [24] to adjust message sending rate dynamically. The constant threshold sometimes cannot reflect the current network status which might cause the inaccuracy of control. GODFREY et al [25] used ACK as the sign to adjust the message sending speed. When node derives the feedback of message loss, it directly rollbacks the sending speed to that the message was successful delivered recently.
The above methods cannot control congestion from the overall situation which needs to build the global feedback control system [26]. Due to the delay as the specific attribute in DTN, the control effect of ACK always has lag phenomenon and congestion identification mistake. Meanwhile, it might cause the severe jitter of message sending speed which leads to the instability of message transfer ratio in DTN. If Nyquist criterion [27] is used in the feedback control system, the instability of message transfer ratio in system is mostly resolved.
The individuals in social group need frequent interaction, interdependence with each other, stable relationship, common interest and unified specification. All nodes in DTN satisfy the most of these properties. DTN environment can be regarded as a social group to study. In this work, the restraint of attacks from malicious nodes can be generalized to cooperation and competition relationships among nodes.
In conclusion, the previous algorithms have not sufficiently considered the routing and the congestion prevention from this perspective. The congestion is always removed passively but not actively avoided. When malicious nodes exist, this passive removal method always does not achieve the anticipative effects. The node’s active defense feature advocated in social psychology and contradiction equilibrium effect in game theory can be integrated to resolve this problem. This can effectively restrain the attacks from malicious nodes and achieve the target of all DTN nodes’ mutual cooperation for the message successful delivery. A new congestion control routing algorithm is proposed from the aspect of establishing stable node relationships to optimize the overall performance of network routing and congestion control in DTN.
3 CRSG algorithm
3.1 Problem description
Node in DTN is distributed discretely and adopts random routing. Random routing results in randomness of node’s encounter to a large extent which makes the message successful delivery ratio unpredictable. The previous solutions usually select transfer node based on the encounter history record to improve it.
However, how to program the message delivery strategy has not been considered when there are malicious nodes in the network. The network security of DTN application areas has significant influence on network performance. The attack from malicious node would cause network congestion. The decline of message successful delivery ratio also happens since the occasional growth of regular nodes’ transmission demand might be misinterpreted as the behavior of malicious nodes. The problem tried to resolve how to select active defense strategy to restrain the attacks from malicious nodes and also how to strengthen the cooperation of nodes to reduce their competition.
3.2 Algorithm idea
Due to the similarity of nodes in DTN, they could be regarded as a group. Social relationship and group theory in social psychology can be leveraged to analyze the variation principle of various parameters in the DTN environment. The transition from competitive goal structure of individual activity to cooperative goal structure of group activity [28] is realized ultimately. Only if making the group goal and most of the individual goals consistent and using the corresponding specification to implement it, cohesiveness [29] of the whole DTN group is enhanced and the DTN group performance [30] is improved eventually.
The behavior characteristic of malicious node corresponds to that of the selfish node. When the selfish nodes exist in DTN, they would result the occurrence of conflict caused by their uncontrolled usage of shared resources. This conflict is triggered through the specific behavior [31] in social relationship. Thus, it causes the emergence of social dilemma. In social dilemma [32], the most favorable short-term behavior of the individual would eventually lead to the negative impact on the group. The short-term interests of individual are opposed to the long-term interests of group. The loss of group long-term interest would eventually result in the loss of individual long-term interest.
Social dilemma is an active field of social psychology research. The most common description is Prison Dilemma [33] and truck games [34]. In Prison Dilemma, when the prisoners face cooperation and competition, they always choose to compete. But actually the cooperation makes their interests achieve maximum. The interactive manner of individuals within a group has a great impact on the group cohesiveness in which competition and cooperation are the main forms of interactive manner. Thus, how to get rid of this unfavorable result to group in practical applications is usually concerned by the researchers.
First of all, the most direct mode is communications among all the parties [35], but it is difficult to achieve in DTN. In addition, the interesting mode is to establish certain regulations of incentive and punishment. For instance, the law of value in economics can be used to automatically optimize the node behavior of group. Meanwhile, group size has influence on social dilemma to a certain extent [36]. In larger group, few individual selfish behaviors are often ignored. Meanwhile, the conformity imitation behavior [37] among individuals of group corrects the few selfish individuals to change their selfish behaviors to some extent. The most effective way is the establishment of corresponding reciprocal rule [38]. The interest of group can be maximized by forcing individuals of group to comply with the rule from the institution.
In the special circumstance of few nodes, selfish behaviors always have an inestimable negative impact on the group without the control of specific rules in DTN. At the same time, behavior imitation among individuals actually forms a set of effective unspoken rule. The individual which does not comply with the rule would be eliminated. In DTN, such rule should be made for the node to balance the reasonable resource occupation among all nodes. Nash equilibrium theory of game theory is adopted to achieve this equilibrium.
The application environment of DTN is mostly serious and it has the characteristic that supply and demand of multi-resource are tense. This would inevitably lead to the competition for resources of each node under one environment. Game theory has obvious advantage to balance the interests of all parties. This theory is used to design the rational parameters that represent the competed resources under the environment. Through the analysis of relationship among parameters, formal formula is derived. Then, the optimization and derivation of formula can extract the bottleneck items. Finally, the balance point among multiple bottlenecks is displayed through the visualization graphic mode to achieve the target of resource rational allocation.
3.3 Algorithm implementation
From the perspective of social psychology, social relationship can be divided into exchange relationship and communal relationship [39]. Communal relationship always exists among intimate individuals. And the individual does not require the reciprocal return from the other peer which represents dedication. On the contrary, in exchange relationship, individuals are unfamiliar with each other and demand the reciprocal return in order to survive.
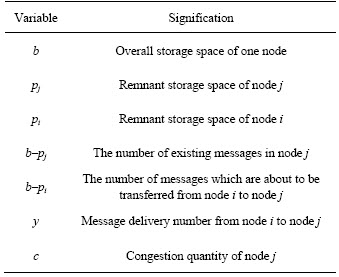
Obviously, in the DTN environment, the relationships among nodes are relatively unfamiliar and even there are malicious or other selfish nodes. Thus, it is finally considered that exchange relationship is used as the relationship among nodes in DTN. In the below, communal relationship is first adopted, then checking out what kind of influence it has on the overall DTN performance through this process. From the perspective of storage resource, it only considers reducing receiver’s congestion ratio at first and then only enhancing sender’s message successful delivery ratio is taken into account. Assume node i encounters j, set i as the sender and j as the receiver. The variables used are listed in Table 1.
Table 1 Variables used in theorems
Theorem 1: When two nodes encounter, if the policy that only guarantees no congestion is adopted, the message successful delivery ratio in the extreme situation would reduce by 50% on average.
Proof: The various classes of relations between pi and pj are shown in Fig. 1.
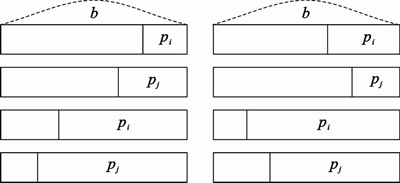
Fig. 1 classes of relations between pi and pj
 c=0, it should be guaranteed that no congestion occurs which means no packet loss happens.
c=0, it should be guaranteed that no congestion occurs which means no packet loss happens.
∴y=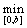 {b–pi, pj }
{b–pi, pj }
Figure 2 shows the change of message delivery number from node i to node j when pi≥pj in the ideal status.
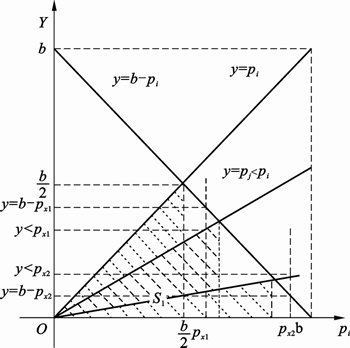
Fig. 2 Change of message delivery number from node i to node j when pi≥pj in ideal status
When 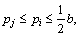
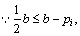
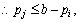
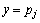 .
.
When pi>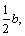
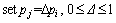 .
.
When 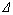 is constant, if
is constant, if 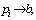 then b–pi=e→0 and pj gradually increases.
then b–pi=e→0 and pj gradually increases.
This makes pj>b–pi,

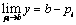 .
.
In Fig. 2, the area of shadow zone S1 represents the variation range of y=pj. The triangle area with S1 which is consisted of straight line y=b–pi, y=pj, and y=0 represents the variation range of Σy. With the reduction of △, the triangle area Σy decreases. Compared to that of y=b–pi which is always used as the message delivery number, the message successful delivery ratio of sender is reduced by at most 100% and at least 50% of which the average reduction is 75% in the extreme situation.
Figure 3 shows the change of message delivery number from node i to node j when pi≤pj in the ideal status.
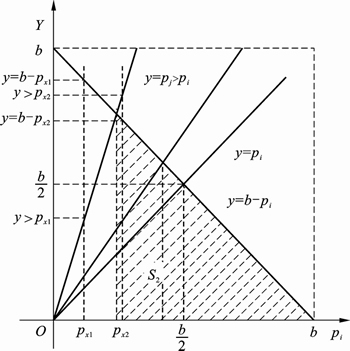
Fig. 3 Change of message delivery number from node i to node j when pi≤pj in ideal status
When 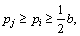
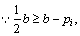
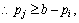
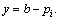
When pi<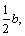
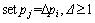 .
.
When 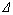 is constant, if
is constant, if 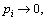 then
then 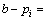
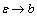 and pj gradually reduces.
and pj gradually reduces.
This makes b–pi> pj ,
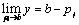 .
.
In Fig. 3, the area of shadow zones S2 represents the variation range of y=b–pi. The triangle area with S2 consisted of straight line y=b–pi, y=pj and y=0 represents the variation range of Σy. With the increase of 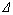 , the triangle area Σy is enhanced. Compared to that of y=b–pi which is always used as the message delivery number, the message successful delivery ratio of sender is reduced by at most 50% and at least 0% of which the average reduction is 25% in the extreme situation.
, the triangle area Σy is enhanced. Compared to that of y=b–pi which is always used as the message delivery number, the message successful delivery ratio of sender is reduced by at most 50% and at least 0% of which the average reduction is 25% in the extreme situation.
To synthesize the situation in Figs. 2 and 3, the message successful delivery ratio in the extreme situation can be reduced by 50% on average.
Theorem 2: When two nodes encounter, if the policy that only guarantees the message successful delivery ratio is adopted, the congestion ratio in the extreme situation would increase by 50% on average.
Proof: Only the increase of message successful delivery ratio is considered which represents that node i would transfer messages to node j as many as possible. In the extreme situation, node i would transfer all the messages it possesses to node j.
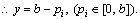
The receiver’s congestion quantity can be derived as c=pj–(b–pi) from Fig. 4. If c adopts negative value, congestion happens. On the contrary, positive value represents no congestion. In the extreme situation, it can be derived that congestion quantity is the straight line represented by c=pi–b (pj=0). The best situation is that congestion quantity coincides with the straight line represented by c=pi (pj=b). The congestion quantity varies from c=pi–b to c=pi. The shadow area represents the distribution of congestion existence status.
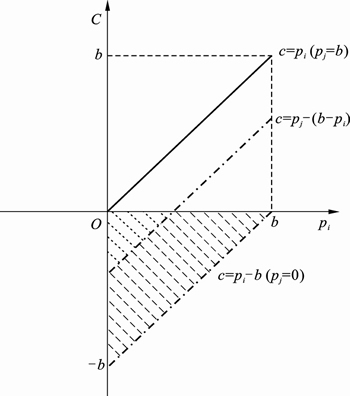
Fig. 4 Change of congestion quantity of node j
Apparently, the distribution of congestion quantity is the parallelogram consisted of pi=0, pi=b, c=pi–b and c=pi. The shadow area of existing congestion occupies the half of parallelogram. This means that compared to that of y≤pj which is always used as the message delivery number, the congestion ratio in the extreme situation increases by 50% on average.
In the stable structure of social exchange relationship, the satisfaction degree of society member in social psychology is reflected by their feeling of fairness. In order to achieve the stability of social relationship in social psychology, the fair principle adopted is always that the income is proportional to the contribution [40]. At the start, individual usually wishes to maximize own interest. But such behavior always tends to make the other individuals feel unfair to produce unhappiness. They would try to restore fairness through actions. Eventually, the fair allocation rule is continuously optimized to make all individuals to comply with it. If it is unable to form, the only way is to end the relationship or some individuals having higher level social right [41].
The nodes in DTN satisfy the conditions required by right balance. 1) Each node has the same storage space, i.e., the amounts of relative resources are equal. 2) They have the same keen extent for the completion of message delivery which meets the principle of least interest [42]. 3) The characteristics of nodes are consistent which means there are no special social norms for the nodes. This relationship would never end yet which means DTN breakdown. Only the formation of fairness can maximize the interest of group in DTN. Fairness is indicated through the fair occupancy of storage resource by all nodes in a stable DTN system. Nash equilibrium theory in game theory would be leveraged to find out the balance point of storage occupancy in DTN.
The memory of each node in DTN is mostly occupied by two types of messages: existing messages in this node and messages which are about to be transferred to this node. Malicious node always unlimitedly demands other nodes to transfer its brought messages and this easily results in the congestion. But under the condition that malicious nodes and normal nodes cannot be distinguished, if only the strategy of resisting the message transfer is adopted, the message successful delivery ratio would be reduced.
Nash equilibrium in game theory[15] is adopted to tradeoff the share of node storage resource between existing messages in this node and messages which are about to be transferred to this node. Active defense is adopted to guarantee the normal message transfer and restrain the attack from malicious node. In this way, the message successful delivery ratio is enhanced and network congestion ratio is reduced as well.
Game theory is applied to the message transfer scenario under malicious node attack. To make use of Nash equilibrium [15], it assumes:
Attendee: node i and node j.
Action: pi and pj.
Preference: b–pi or b–pj is expected to be maximized, i.e., each node expects its messages to acquire more transferring opportunities until these messages reach the destination nodes.
Due to the existence of preference, nodes in the network compete with each other for storage resource. Especially, the existence of malicious nodes aggravates this phenomenon. This inevitably results in the contradiction between the increase of message successful delivery ratio and the reduction of congestion ratio. Nash equilibrium theory is helpful to find out the balance point of all parties’ preference and mitigate this contradiction to optimize the interest of whole system in DTN.
Theorem 3: By leveraging the fairness theory in social exchange relationship and integrating with Nash equilibrium for computation, the message successful delivery ratio can be guaranteed and the congestion can also be controlled well in DTN.
Proof: According to the fairness theory in social exchange relationship of social psychology [14], we have
b–pi=b–pj pi=pj (1)
pi=pj (1)
According to liability compartmentalization theory [43] in Nash equilibrium [15], the following can be derived. :
From the perspective of node j, the node i’s liability of its congestion is 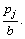
From the perspective of node i, its liability of node j’s congestion is 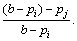
From the global view, once congestion happens at node j, the liability that node j reckons node i should take is equal with that node i reckons itself should take.
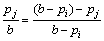 (2)
(2)
According to Eqs. (1) and (2), it can be derived
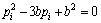 (3)
(3)
According to Eq. (3), it can be derived
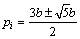
Due to 0≤pi≤b, pi adopts the value in the reasonable range as the below
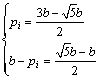 (4)
(4)
According to Eq. (1), it can be derived:
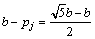 (5)
(5)
The above proof is shown in Fig. 5.
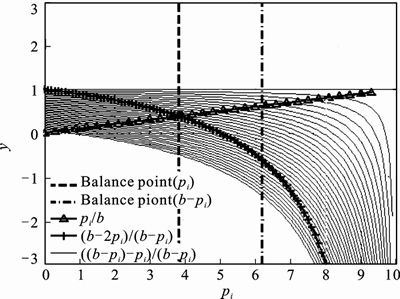
Fig. 5 Reasonable balance point of storage occupancy by nodes
According to Eqs. (4) and (5), it can be derived that the number of existing messages in node j is the same as the number of messages which are about to be transferred from node i to node j and these two values are both in the reasonable span. This means that there is a reasonable balance point of storage occupancy by nodes in DTN.
Nash equilibrium points out that if the balance point exists in system, it indicates that the whole system interest can achieve optimization at this time.
Therefore, when all the nodes are controlled by the threshold of this balance point and they conform to the fair occupancy of storage resource, the message successful delivery ratio can be guaranteed and the congestion can also be controlled well in DTN.
4 Evaluation
From the interpretation of aggression in social psychology [44], it could be derived that the competition influences effectiveness and intensity of individual attack to some extent [45]. More intense competition would result in more severe attack and more obvious attack effect. This theory was leveraged in our work. In the experiment environment existing malicious nodes, it should set less node storage, faster node movement, and more frequent message generation rate. Thus, the congestion caused by the attacks to the storage from malicious nodes could be exhibited in the shorter experiment time.
As the measure for controlling the attack behavior, the method of pre-intervention in social psychology was adopted. And the optimal balance control point could be obtained through Nash equilibrium in game theory. The congestion control routing algorithm for security defense was designed based on social psychology and game theory. The routing algorithm without using the pre-intervention based on the encounter history information which only deletes the oldest message here was named as EHR. The DTN-dedicated simulator THE ONE was leveraged to compare CRSG with HER in the congestion ratio and the message successful delivery ratio.
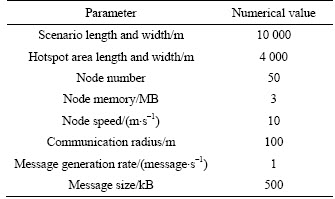
The parameters in the experiment are set as Table 2.
Table 2 Simulation parameters
The experiment was designed to prove the conclusion. This should verify the CRSG’s influence on the variation of congestion ratio and message successful delivery ratio. In the below, experiment grouping was well devised according to the variation of congestion ratio. According to the characteristic in social psychology that productivity variation was influenced by both group cohesiveness and group goal concentrate degree [46–47], the corresponding parameters were defined in DTN as shown in the below:
Productivity variation (py): the variation quantity of congestion ratio(cr);
Group cohesiveness (cs): whether to control the message amount of node receiving or delivery. Group cohesiveness was higher if CRSG algorithm was employed.
Group goal concentrate degree (gl): the contrast degree of node attributes in two experiments. If the contrast degree was larger, group goal concentrate degree was higher. The goal here was to prove the algorithm validity with the existence of malicious node. Thus, in two experiments, the number difference of normal nodes and malicious nodes was larger, i.e., the contrast degree was larger, group goal became more concentrated.
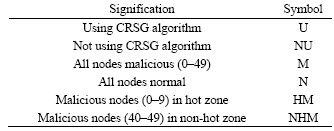
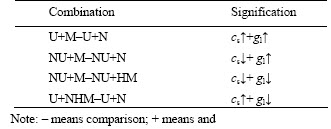
Therefore, four comparison groups were designed that each one was consisted of two experiments. The symbols used in the experiment are listed in Table 3 (0–49 was the node serial number. The number in parentheses was the malicious node serial number such as (0–9)).
Table 3 Explanation of symbols used in experiment
The grouping status is given in Table 4.
Table 4 Meanings of comparative experiments in group theory
The experiment results are shown in Fig. 6. The parameter that was compared in the grouping experiment was cr (%). Table 5 could be derived.
Group cohesiveness and group goal concentrate degree influenced productivity variation as shown in Table 6. Our results matched its conclusion through comparing Tables 4 and 5 with 6. Therefore, our experiment design was reasonable and the conclusions of algorithm were correct, which achieved the expected effect of adopting social psychology and game theory.
Table 5 Influence of comparative experiment groups on congestion ratio variation
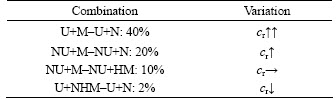
Table 6 Productivity variation influenced by group theory factors

In the below, the influence of CRSG compared to EHR on the congestion ratio and message successful delivery ratio was further analyzed.
As shown in Fig. 6, it could be found that CRSG significantly improved the network congestion compared with EHR in DTN. Based on Nash equilibrium theory in game theory, the threshold balance point could be set between the number of existing messages and the number of messages which were about to be transferred. This forcefully restricted malicious nodes from the storage resource consumption of the other nodes. The congestion caused by the uncontrolled occupation was improved and the limited storage resource was rationally utilized in the form of share. Thus, it effectively reduced the congestion ratio of DTN group.
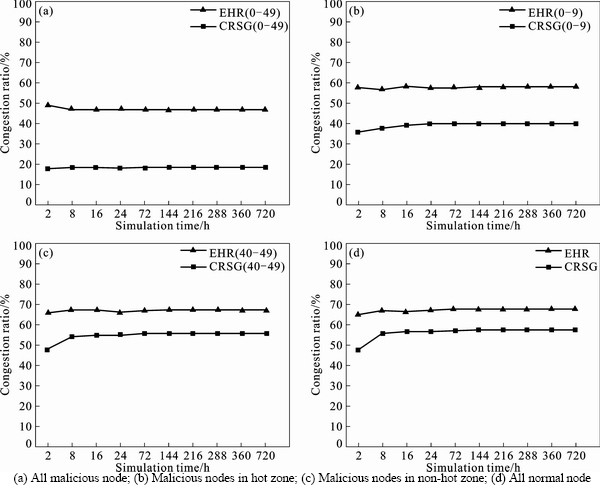
Fig. 6 Congestion ratio:
In the experiment, the shorter message generation interval was designed to make the congestion effect more obvious in a short time. Meanwhile, DTN had the characteristics of intermittent connection and packet loss caused by congestion. The above aspects resulted that the message successful delivery ratio in this experiment was not high. But this had no influence on the superiority reflection of our designed algorithm. Through the comparison of message successful delivery ratio in Fig. 7, it could be seen that CRSG compared with EHR increased the message successful delivery ratio. The message in DTN must leverage the node multi-hop transfer to achieve successful delivery. Due to the storage consumption by malicious nodes, congestion caused that parts of messages couldn’t be normally delivered to the destination node since they might be deleted halfway. CRSG limited this consumption well and avoided the halfway message deletion in some extent. It enhanced the message successful delivery ratio.
To compare the congestion ratio of CRSG or EHR in Fig. 6, it would be found that the congestion ratio reduced inversely when the number of malicious node increased. Under the same group cohesiveness, it could be found out that the required hops of message successful delivery increased along with the number growth of malicious node in Fig. 8. The congestion ratio was computed by that packet loss number l due to the congestion was divided by the total message transfer number t. It assumed that the congestion ratio l/t and the experienced average hops before packet loss was h under the condition that there were a certain number of malicious nodes. When the number of malicious node was increased, l was increased by Δ. At this time, the hop count was H>h, t increased more than Δ×(H h). Obviously, the increase of malicious nodes enhanced l by a smaller extent than t. It was easy to prove that the congestion ratio would contrarily reduce with the growth of malicious nodes. But in fact, the number of congestion occurrence was enhanced.
h). Obviously, the increase of malicious nodes enhanced l by a smaller extent than t. It was easy to prove that the congestion ratio would contrarily reduce with the growth of malicious nodes. But in fact, the number of congestion occurrence was enhanced.
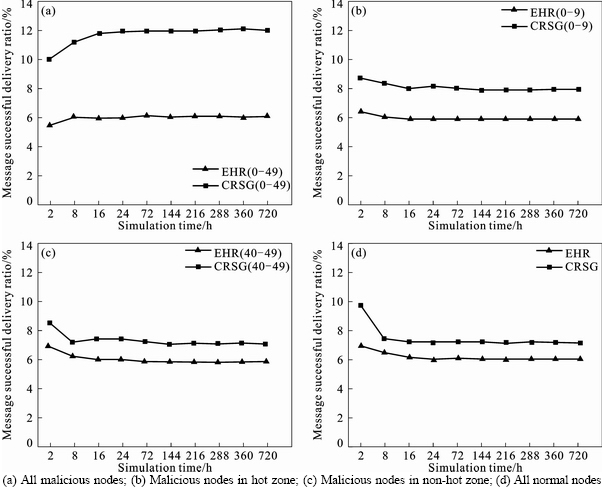
Fig. 7 Message successful delivery ratio:
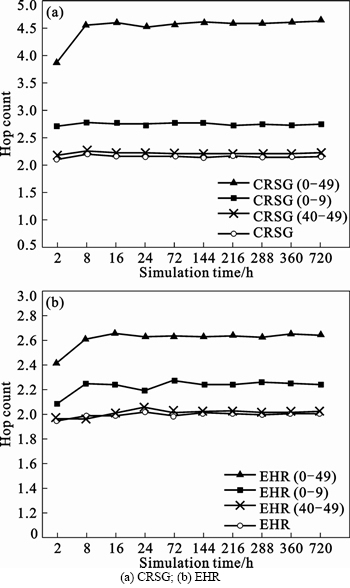
Fig. 8 Hop count:
From the perspective of social impact theory [48], the above phenomena could be explained yet. Quantity, intensity and directness of impact source decided how much the target was influenced. When multiple impact sources attacked one target, the effect would be strengthened. But when one impact source attacked multiple targets, the effect would be dispersed. In our experiment, as shown Figs. 6 and 7, if there were more
malicious nodes, the effect of CRSG algorithm was more obvious. The above result reflected the feature of quantity. The impact effect of malicious nodes in the hot zone was stronger than that in the non-hot zone which reflected the feature of directness. However, the parameters of some attributes such as priority and storage were the same for the malicious node and normal node which represented the impact intensity was the same.
5 Conclusions
1) a new congestion control routing algorithm for security defense based on social psychology and game theory is proposed on the premise that malicious nodes perform attacks by consuming storage in DTN. Cooperation represents that the result is not only beneficial to oneself but also to the others through the interactions. Competition represents one party only considers increasing the interest of oneself regardless of the damage to the interest of others. The algorithm mainly leverages the ideas of social relationship and group theory in social psychology to analyze how to resolve the contradiction relationship of competition and cooperation reflected through the inherent selfishness of each node for the delivery ratio enhancement and the network overall performance improvement in DTN. Through learning ideas from Nash equilibrium in game theory, setting specific threshold can balance the amount of existing messages and messages which are about to be transferred and make them share the node storage resource. This results in that all nodes share the storage resource fairly and strengthens their cooperative relationship. This algorithm guarantees the transfer operation of normal nodes for message successful delivery and effectively restrains the malicious node from illegal occupancy of the node storage. Through the design of comparison experiment based on theories in social psychology, this proves effectively that the algorithm guarantees the message successful delivery ratio and controls the network congestion. Therefore, the contradiction relationship of above two network performance target can be well resolved.
2) The research would be continued on active defense mechanisms to all kinds of attacks from malicious node. The message successful delivery ratio should be guaranteed. The mechanism also should perfect congestion control, optimize the defense effect and effectively decrease the message delivery delay. In next step, the influence would be discussed about other attack behaviors from the malicious node in DTN. The corresponding defense method would be proposed.
References
[1] DTNRG: Delay-tolerant networking research group [EB/OL] 2012–07–01. http://www.dtnrg.org.
[2] Pentland A S, Fletcher R, Hasson A. Dak Net: Rethinking connectivity in developing nations [J]. Computer, 2004, 37(1), 78–83.
[3] Burgess J, Gallagher B, Jensen D, Levine B N. Maxprop: routing for vehicle-based disruption-tolerant networks [C]// Proceedings of INFOCOM, Barcelona, 2006: 1–11.
[4] Burleigh S, Hooke A, Torgerson L, Fall K, Cerf V, Durst B, Scott K. Delay-tolerant networking: an approach to interplanetary internet [J]. IEEE Communications Magazine, 2003, 41(6): 128–136.
[5] Scott K, Burleigh S. Bundle protocol specification [R] Mclean, Virginia: Internet RFC 5050, 2007.
[6] Fall K, Hong W, Madden S. Custody transfer for reliable delivery in delay tolerant networks [R]. Berkeley: Intel Research, IRB-TR-03-030, 2003.
[7] Vahdat A, Becker D. Epidemic routing for partially connected ad hoc networks [R]. Durham: Duke University, CS-2000-06, 2000.
[8] Lindgren A, Doria A, Schelén O. Probabilistic routing in intermittently connected networks [J]. SIGMOBILE Mobile Computing Communications Review, 2003, 7(3): 19–20.
[9] Jain R, Ramakrishnan K K. Congestion avoidance in computer networks with a connectionless network layer: concepts, goals, and methodology[C]// IEEE Comp Networking Symp, Washington DC, 1988, 134–143.
[10] Seligman M, Fall K, Mundur P. Storage routing for DTN congestion control [J]. Wireless communications and mobile computing, 2007, 7(10), 1183–1196.
[11] Hollot C V, Misra V, Towsley D, Gong W B. A control theoretic analysis of RED [C]// IEEE INFOCOM, Anchorage, 2001: 1510–1519.
[12] Feng L, Jie W, Avinash S. Thwarting black hole attacks in disruption-tolerant networks using encounter tickets [C]// IEEE INFOCOM, Rio de Janeiro, 2009: 2428–2436.
[13] Vivek N, Yi Y, Sencun Z. Resource-Misuse attack detection in delay-tolerant networks [C]// Performance Computing and Communications Conference (IPCCC), IEEE, University Park, 2011: 1–8.
[14] Taylor S E, Peplau L A, Sears D O. Social psychology 10th Edition [M]. New York: Pearson Education Press, 1993.
[15] Osborne M J. An Introduction to game theory [M]. Oxford: University Press, 2004.
[16] Spyropoulos T, Psounis K, Raghavendra C S. Spray and wait: an efficient routing scheme for intermittently connected mobile networks [C]// Proceedings of the 2005 ACM SIGCOMM workshop on Delay-tolerant Networking(WDTN '05), 2005, New York, NY, USA: ACM, 252–259.
[17] Spyropoulos T, Psounis K, Raghavendra C S. Efficient routing in intermittently connected mobile networks: the multiple-copy case [J]. IEEE/ACM Transactions on Networking, 2008, 16(1), 77–90.
[18] Zhao W, Ammar M, Zegura E. A message ferrying approach for data delivery in sparse mobile ad hoc networks [C]// Proc of the ACM Mobihoc, Roppongi, 2004, 187–198.
[19] Costa P, Mascolo C, Musolesi M, Picco G P. Socially-Aware routing for publish-subscribe in delay-tolerant mobile ad hoc networks [J]. IEEE Journal of Selected Areas in Communication, 2008, 26(5): 748–760.
[20] Floyd S, Jacobson V. Random early detection gateways for congestion avoidance [J]. IEEE/ACM Transactions on Networking, 1993, 1(4): 397–413.
[21] Seligman M, Fall K, Mundur P. Alternative custodians for congestion control in delay tolerant networks [C]//. SIGCOMM Workshops, Pisa, Italy. 2006: 229–236.
[22] TAO Yong, GONG Zheng-hu, LIN Ya-ping, ZHOU Si-wang. Congestion aware routing algorithm for delay-disruption tolerance networks [J]. Journal of Central South University of Technology, 2011, 18(1): 133–139.
[23] Nishiyama H, Ansari N, Kato N. Wireless loss-tolerant congestion control protocol based on dynamic aimed theory [J]. IEEE Wireless Communications, 2010, 17(2): 7–14.
[24] Chiu D M, Jain R. Analysis of the increase and decrease algorithms for congestion avoidance in computer networks [J]. Computer Networks ISDN Sys, 1989, 17, 1–14.
[25] Godfrey P B, Schapira M, Zohar A, Shenker S. Incentive compatibility and dynamics of congestion control [C]// SIGMETRICS, New York, USA, 2010: 95–106.
[26] Firoiu V, Borden M. A Study of active queue management for congestion control [C]// IEEE INFOCOM, Tel Aviv, 2000: 1435–1444.
[27] Paganini F, Wang Z K, Doyle J C, Low S H. Congestion control for high performance, stability, and fairness in general networks [J]. IEEE/ACM Transactions on Networking, 2005, 13(1), 43–56.
[28] Deutsch M. An Experimental study of the effects of cooperation and competition upon group process [J]. Human Relations, 1949, 2(3): 197–292.
[29] Cota A A, Evans R C, Dion L K, Kilik, L, Longman, S R. The structure of group cohesion [J]. Personality and Social Psychology Bulletin, 1995, 21(6): 527–580.
[30] Gowen C R. Managing work group performance by individual goals and group goals for an interdependent group task [J]. Journal of Organizational Behavior, 1986, 7(3): 5–27.
[31] Braiker B H, Kelley H H. Conflict in the development of close relationships. In Burgess R L, Huston T L (Eds.), Social exchange in developing relationships [M]. New York: Academic Press, 1979: 256–280.
[32] Brewer, B M, Kramer, M R. Choice behavior in social dilemmas: Effects of social identity, group size, and decision framing [J]. Journal of Personality and Social Psychology, 1986, 50(3): 543–549.
[33] Luce D R, Raiffa H. Games and decisions [M]. New York: Wiley Press, 1957: 87–126.
[34] Deutsch M, Krauss R M. The effect of the threat on interpersonal bargaining [J]. Journal of Abnormal and Social Psychology, 1960, 61(1): 181–189.
[35] Orbell M J, van de Kragt, C A J, Dawes M R. Explaining discussion induced cooperation [J]. Journal of Personality and Social Psychology, 1988, 54(5): 811–819.
[36] Glance S N, Huberman A B. The dynamics of social dilemmas [J]. Scientific American, 1994, 270(3): 76–81.
[37] Cialnidi R B, Trost M R. Social influence: social norms, conformity, and compliance. In Gilbert D T, Fiske S T, Lindzey G(Eds.), Handbook of social psychology [M]. Boston: MA: McGraw-Hill Press, 1998: 151–192.
[38] Tyler R T, Degoey P. Collective restraint in social dilemmas: Procedural justice and social identification effects on support for authorities [J]. Journal of Personality and Social Psychology, 1995, 69(3): 482–497.
[39] Clark S M, Mills J. Interpersonal attraction in exchange and communal relationships [J]. Journal of Personality and Social Psychology, 1979, 37(1): 12–24.
[40] Deutsch M. Distributive justice: A social psychological perspective [M]. New Haven, CT: Yale University Press, 1985: 122–155
[41] Huston L T, Kelley H H. close relationships [M]. New York: W. H. Freeman Press, 1983: 169–219.
[42] Willard W Reuben H. The family: a dynamic interpretation [M]. Ft Worth, Tx, Us: Dryden Press, 1951: 437–482.
[43] Brown John P. Toward an economic theory of liability [J]. Journal of Legal Studies, 1973, 2(2): 323–349.
[44] Buss H A, Perry M. The aggression questionnaire [J]. Journal of Personality and Social Psychology, 1992, 63(3): 452–459.
[45] Anderson A C, Morrow M. Competitive aggression without interaction: Effects of competitive versus cooperative instructions on aggressive behavior in video games [J]. Personality and Social Psychology Bulletin, 1995, 21(10): 1020–1030.
[46] Schachter S. The psychology of affiliation [M]. Stanford: CA: Stanford University Press, 1959: 21–35.
[47] Schachter S. The interaction of cognitive and physiological determinants of emotional state. In L. Berkowitz (Ed.), Advances in experimental social psychology [M]. New York: Academic Press, 1964: 49–80.
[48] Latane B. The psychology of social impact [J]. American Psychologist, 1981, 36(4): 343–356.
(Edited by HE Yun-bin)
Foundation item: Projects(61202488, 61070199, 61103182) supported by the National Natural Science Foundation of China
Received date: 2012–07–20; Accepted date: 2012–10–20
Corresponding author: WANG Cheng-jun, PhD; Tel: +86–13677381004; E-mail: cjwmhd@gmail.com

