Prediction-based energy-efficient target tracking protocol inwireless sensor networks
来源期刊:中南大学学报(英文版)2010年第2期
论文作者:BHUIYAN M. Z. A 王国军 张力 彭勇
文章页码:340 - 348
Key words:wireless sensor networks; target tracking; wakeup mechanism; face-aware routing; energy efficiency
Abstract: A prediction based energy-efficient target tracking protocol in wireless sensor networks (PET) was proposed for tracking a mobile target in terms of sensing and communication energy consumption. In order to maximize the lifetime of a wireless sensor network (WSN), the volume of messages and the time for neighbor discovery operations were minimized. The target was followed in a special region known as a face obtained by planarization technique in face-aware routing. An election process was conducted to choose a minimal number of appropriate sensors that are the nearest to the target and a wakeup strategy was proposed to wakeup the appropriate sensors in advance to track the target. In addition, a tracking algorithm to track a target step by step was introduced. Performance analysis and simulation results show that the proposed protocol efficiently tracks a target in WSNs and outperforms some existing protocols of target tracking with energy saving under certain ideal situations.
基金信息:the Hunan Provincial Natural Science Foundation, China
Program for New Century Excellent Talents in University
Program for Changjiang Scholars and Innovative Research Team in University
J. Cent. South Univ. Technol. (2010) 17: 340-348
DOI: 10.1007/s11771-010-0051-1 ![]()
BHUIYAN M. Z. A., WANG Guo-jun(王国军), ZHANG Li(张力), PENG Yong(彭勇)
School of Information Science and Engineering, Central South University, Changsha 410083, China
? Central South University Press and Springer-Verlag Berlin Heidelberg 2010
Abstract: A prediction based energy-efficient target tracking protocol in wireless sensor networks (PET) was proposed for tracking a mobile target in terms of sensing and communication energy consumption. In order to maximize the lifetime of a wireless sensor network (WSN), the volume of messages and the time for neighbor discovery operations were minimized. The target was followed in a special region known as a face obtained by planarization technique in face-aware routing. An election process was conducted to choose a minimal number of appropriate sensors that are the nearest to the target and a wakeup strategy was proposed to wakeup the appropriate sensors in advance to track the target. In addition, a tracking algorithm to track a target step by step was introduced. Performance analysis and simulation results show that the proposed protocol efficiently tracks a target in WSNs and outperforms some existing protocols of target tracking with energy saving under certain ideal situations.
Key words: wireless sensor networks; target tracking; wakeup mechanism; face-aware routing; energy efficiency
1 Introduction
Wireless sensor networks distinguish themselves from other traditional wireless or wired networks through sensor and actuator based on interaction with the environment [1]. Energy efficiency is one of the most important research issues in wireless sensor networks since it determines the lifetime of the sensor network deployed for the intended applications, such as environmental monitoring, area surveillance and target tracking.
Target tracking with energy saving is one of the most critical issues in wireless sensor networks. A variety of energy conservation methods for target tracking sensor networks were devised by LIN and TSENG [2], XU et al [3], JAEHOON et al [4], XING et al [5] and BHUIYAN et al [6]. In this paper, prediction-based cooperative target tracking in sensor networks was focused. Some prediction-based methods [7-9] were presented to predict the location of mobile targets and to allow a limited number of sensors to track a target. The use of mobile agents with predictable mobility for tracking system is interesting in WSNs where the agent moves between sensors with the tracking data [10-12]. Mobicast routing protocols using sensor networks were mainly designed by HUANG et al [13-14] for predicting the target moving direction. Although all the aforementioned methods were creative works focusing on prediction based tracking, they did not consider prediction based cooperative tracking and used a large number of active sensors.
In the previous research [15] for target tracking, two algorithms were demonstrated, namely, RARE-Area and RARE-Node to reduce the number of nodes participating in tracking and increase energy efficiency. A novel target tracking protocol using sensor networks was proposed by TSAI et al [16] for mobile users. It was assumed that a mobile target may move in any way, so in all the ways the sensors need to be active. In this case, the proposed protocol consumes more energy and induces larger information collecting delay that results in wakeup delay, which can lead to large message delay.
The cooperation is an important issue for target tracking. Cooperative tracking algorithms using binary-detection sensors were suggested by KIRILL et al [17] and RAJEEV et al [18] to track the target with higher precision and accuracy. This cooperative tracking approach requires only that a sensor is able to determine whether or not a target is somewhere within the maximal detection range of the sensor, but its target missing rate is very high.
A prediction-based energy-efficient target tracking protocol (PET) was put forward for deriving the target moving path and utilizing the target moving patterns for energy saving prediction-based target tracking sensor networks. The salient characteristics of the cooperative tracking protocol were that it achieved better resolution than that with a lot of sensors being used and provided earlier estimation of the target’s position, direction and velocity. However, not all sensors or partial sensors may have useful information; hence, an informed selection of sensors with the best data for cooperation can save power. The PET uses a primary sensor that is in the active state and the secondary sensors are in the awake state. The protocol significantly simplified the beacon’s calculation and minimized the volume of messages exchanged between beacons as well as sensors and trackers.
2 Problem formulation
In order to maximize the lifetime of the sensor network, an energy-aware target tracking method based on sensors cooperation that allows a minimal number of sensors near the target to work in both communication and sensing was proposed. It is known that the accuracy of tracking is strongly influenced by the number of active sensor nodes in a sensor network. If the number of active sensors is large, the accuracy will be higher. However, energy consumption could also be high because energy utilization is proportional to the number of active sensor nodes. Conversely, a smaller subset of sensors may lead to inaccurate tracking. In this PET protocol, an elected sensor in a particular area only will become active if it is informed to be active; and other requested sensors cooperate with that sensor. When a sensor detects a moving target in its sensing range, it will transmit the location information to its neighbors. When moving, the target may non-deterministically move to a neighbor. So the detecting sensor contacts the neighbors and checks if it is the closest sensor to the target, then the closest sensor confirms the previous sensor and becomes an active sensor. The PET uses an energy-efficient wakeup mechanism to shorten the grasp time. The sensors can be cooperated to adjust the route between the target and the tracker dynamically. This cooperative tracking protocol improves accuracy by comparing information from several nodes rather than relying on one node only.
2.1 Assumptions and definitions
There are several assumptions in this target tracking protocol design as follows.
The tracker is assumed to be a single generic source. A tracker can be a source such as a mobile user, a fire-fighter or others, who wants to track a moving object called target, in a wireless sensor network.
A single target is tracked in a sensor network. The target can be an enemy vehicle, an intruder or the movement of a wild animal, or moving fire as well.
All nodes are able to communicate with their neighbors after initial deployment and know their locations and the locations of their immediate neighbors by self-positioning system [19].
The sensor network is homogeneous, and the sensors are all clock synchronized and randomly distributed in the network in a two-dimensional sensor field [20].
2.2 Models
Each node in a face, which is referred to by some researchers as anchor, locator, or seed nodes [21], is capable of computing. In this work, beacon nodes are used for two purposes: (1) to provide location information to the tracker or target sensor node and, (2) to exchange information with other nodes. A beacon node does not necessarily need to wait passively to hear or inform. The idea of beacon-based localization is presented in Fig.2.
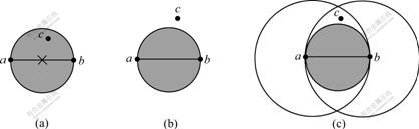
Fig.1 Presence of point c within circle to prevent points a and b from being Gabriel neighbors (a), describe points a and b as Gabriel neighbors (b, c), as point c is outside of their diameter circle

Fig.2 Example of planarized network showing planner face neighbors in planner neighborhood graph to point up tracking path lines between two nodes indicating connectivity between them (Black, grey shaded and white nodes indicate active, awake and inactive states, respectively)
2.2.2 Planarization techniques
The concept of relative neighborhood graph (RNG) and Gabriel graph (GG) [22-23] of a finite planner set of points in the Euclidean plane G is briefly introduced. RNG(G) is a prominent representation of sensor nodes which are defined using some concept of neighborliness. The relative neighborhood graph of a graph G=(V, E), denoted by RNG(G), is the set of all edges ![]() such that there is no vertex or point c where
such that there is no vertex or point c where ![]()
![]() and ||ac||<||ab|| and ||cb||<||ab||. More generally, in any dimension, the Gabriel graph connects any two points, forming the endpoints of the diameter of an empty sphere (as shown in Fig.1). In a unit disk graph, two neighbor nodes have a common edge if and only if their Euclidean distance is less than a constant.
and ||ac||<||ab|| and ||cb||<||ab||. More generally, in any dimension, the Gabriel graph connects any two points, forming the endpoints of the diameter of an empty sphere (as shown in Fig.1). In a unit disk graph, two neighbor nodes have a common edge if and only if their Euclidean distance is less than a constant.
2.2.3 Face structure
This PET is described using above relative neighborhood based on the concept of face-aware routing [14, 24] by assuming that the network is modeled as a unit disk graph and nodes are placed in the two-dimensional Euclidean space.
An order is assigned to the nodes on a face in the clockwise direction (see Fig.2). Given a connected pair of nodes υ1 and υ5 in a planar graph G, assume that every node in G completely knows all its faces. A node does not need to know all of the sensors and their location but face neighbors. Moreover, assume that a node only needs to cooperate with the neighbors of the face in which the target is present.
For example, in Fig.2, node υ1 corresponds to three face neighbors F1, F2, and F18, so node υ1 is contained in and stores information about three faces that are adjacent to it in the planar sub graph: {υ1; υ5; υ6; υ7; υ2}, {υ1; υ3; υ4; υ5} and {υ1; υ2; υ3}. This means that only three immediate graph neighbors of υ1 are υ2, υ3 and υ5, but only the subgraph called face where the target is positioned is considered. In this way, a node has two face neighbors in a face called immediate face neighbors. Suppose the target is in face F2, υ1 then has only two immediate face neighbors that are υ5 and υ2. It is worth mentioning that the PET protocol only needs to use one neighbor depending on the target movement, i.e., υ1 communicates with either υ5 or υ2. In the same way, node υ9 has six adjacent faces with 12 neighbors. If all the faces and nodes corresponding to a node are considered, the network communication cost and energy consumption will be higher.
2.2.4 Wakeup mechanism
In this work, according to the operation of sensors, a sensor node has three different states of operation: active, inactive and awake. Fig.3 gives a general idea of operation mode of nodes in the network. Each sensor node can be in one of the three states. The most efficient energy state is the inactive state in which the sensor turns its service off. A node that is inactive continues remaining in the inactive state until it receives a message from a current beacon or neighboring node. It has no activities such as sensing.
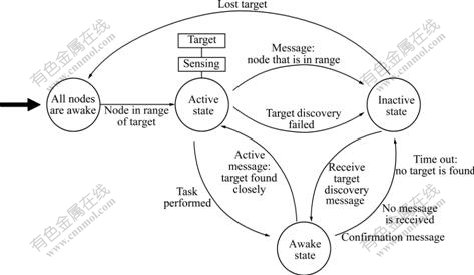
Fig.3 Inclusive state diagram showing all steps of sensor nodes in PET
A predefined time was assumed for sensors to change their state. A sensor periodically wakes in a predefined period and changes it to awake state. In the awake state, sensor’s communication and sensing channel stay in the inactive state and they consume minimal energy most of the time. The communication channel wakes up routinely and checks for request to receive possible messages from the beacon to discover the target. If a sensor has no messages, it will return to the inactive state. A sensor node can only move to the active state when it is in the awake state and ensures that it is the closest to the target. If it is the closest, it will send a message to the current node in the awake state. If the sensor does not change its state to active state in this period, or it does not find the target, its state will return to the inactive state.
While a sensor is in the active state, it will actively participate in the tracking process and waits for the tracker’s or neighbor’s signal. An active node remains active until active time expires as well as receives a confirmation message to change its state. Active time indicates the active period of a beacon. This wakeup mechanism shown in Fig.3 takes advantage of the energy saving feature in sensor networks while the beacons are in the active state one by one, and the other nodes typically stay in a periodically inactive or awake state.
2.2.5 Sensing energy model
There are many ways of target signal processing, for example, acoustic, seismic, and electromagnetic signals. The energy of the signal attenuates with distance between the target and beacon sensor. Beacon sensors detect the target by measuring the energy of omnidirectional signals emitted by targets and converting the signal to an electric signal. When a mobile target moves across a face, a sensor node can detect the physical signals emitted by the target in its sensing area. Suppose the sensor deployed at locations SLm, n (where m=1, 2, …; n=1, 2, …) denote a sensor location coordinates (xm, ym). The signal emitted by the target decreases as the distance from the target increases. se is the energy emitted by the physical size of the target at location OLi. The sensing model can be represented as Si(OLi):
![]() (1)
(1)
where η is an adaptable constant obtained from the target shape. di is the distance between the target and sensor
location, ![]() .The decaying
.The decaying
factor is c and the value c typically ranges from 2.0 to 5.0.
3 Overall target tracking
This subsection discusses the interaction among the tracker, the target and the beacons. The process is illustrated in Fig.4. Tracker T sends a flooding request to the sensor network at time ti, requesting the position of target o. Since the target is in face F1, tracker T is informed of the target’s current location, and the closest sensor is node υ4 (see Fig.4(a)).
In face F1, sensor v4 has three face neighbors that are v5, v1 and v3. But v4 has two immediate neighbors of v5 and v3. If the target moves in the direction of an
immediate neighbor, v4 is able to easily determine an immediate sensor towards which the target is moving. As shown in Fig.4(a), if sensor v4 estimates that the target is moving towards another face neighbor υ1, because target o moves arbitrarily, υ1 will chronicle and compute the information in its local memory. Node υ4 sends the information to the next elected node υ1 in the sensor network that the target is about to move in that direction. Since T arrives at the vicinity of υ4 after the target has moved away, it is also informed by the beacon to follow the same route, i.e., go to υ1. If target o leaves this location at the time when T reaches υ1’s location, T again will send a message containing a request to the next beacon to get the target’s present position.
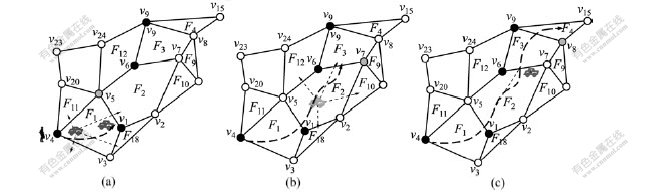
Fig.4 Target tracking in PET: (a) v4 is beacon and senses target in F1; (b) υ1 is beacon and senses target in F2; (c) υ6 is beacon and senses target in F3
If T continually uses a flooding method to get the target position, the sensor’s energy can rapidly wear out. This work offers a protocol that not only saves sensor energy but also allows to capture the target quickly.
When the tracked target moves from face F1 to face F2 along the route indicated in Fig.4(b) at time ti+1, the nearest node υ1 will be already aware of the target route. Node υ1 receives the message from v4 and makes it forwards to its immediate neighbors in F2 (v5 and v2) and then checks itself to confirm if it is the new beacon node. Node υ1 is now in the awake state and detects the target as it moves from face F1 to face F2. When υ1 is in the active state, it senses and observes the target in face F2. Meanwhile, T reaches the position of υ1 and requests for the target status from υ1. Node υ1 works in the aforementioned way and elects υ6 as the next beacon compared with the target future movements at time ti+2. The sequence of beacon nodes represents the target tracks and tracker routes. Target moving sequence may be F1→F2→F3→F4 and so on.
In order to discuss detection failure, suppose that υ7 is currently elected as beacon. If the target is not in the sensing range of υ7, υ7 may fail to detect the target. But in this work, assume that υ7 fails to detect the target, the immediate neighbor υ6 cooperates and then detects the target. If υ6 fails to detect the target, the target may change the direction. υ7 then sends a message to all its face neighbors to cooperate in tracking the target. These neighbors include υ2, υ1, υ5, and υ6 except itself in face F2. If υ7 does not get any reply about target detection, it will send a message to tracker T which in turn also sends a message to the sensor network to relocate the target. This mechanism prevents the chance of routing failure, node failure as well as lost tracking. Additionally, if the target unfortunately stays in a void region while the tracker gets a target missing message, the tracker cannot get the next information and then it tries to relocate the target after a predefined period. When the target leaves the void region, the target can be detected in a face, and its location can be obtained by the tracker.
4 Design of PET protocol
The PET tracking protocol is derived from the cooperation of sensors. Whenever a target is detected, an election process is conducted by the current beacon and nearby sensors to choose a sensor, on which a tracker is initiated to observe the movement behavior of the target. The PET first determines the location of the target, and then uses two-dimensional Gaussian distribution to accurately predict the future location of the target. Once the future location of the target is known, the new become is computed. Based on coordination among the sensor nodes, a node is selected, which uses direct flooding to communicate the information to the new active face.
The following steps describe how the sensor nodes operate with reference to the diagram in Fig.5.

Fig.5 Face and its neighbors directed to next possible closest node of target
(1) Initialization. Initially, there is a target in the sensor network, and all the nodes are in energy-saving mode. The sensor network is synchronization-based and the sensors periodically synchronize to wake and to hibernate. Tracker T needs to track target o, but it does not know the location of target o. Tracker T sends a flooding request message over the sensor network to locate target o. The message is sent in awake period of sensor.
(2) Target detection. After initialization, once the sensor network detects the target, the network selects the sensor node closest to the target as beacon node b. This active node is tuned to send a message to the tracker.
(3) Tracker movement. After detecting the target, the active node generates a detection message, which is composed of the node’s unique id, denoted by node_id and the timestamp of the target signal oSnode_id. Tracker T obtains the target location that is informed from the first beacon node bi. T then starts to move towards the location of the first beacon bi.
(4) Location and direction estimation. There are two things to advance location estimation. The first thing is that a beacon indicates the predicted location where the target can be located after a given period of time. This predicted location is used by the beacon to determine the most likely node to which the target approaches and inform them in advance about the oncoming target. The second thing is that the beacon node can then use this information to direct (see Fig.3) its appropriate sensors for the sensing task. To keep the calculation and communication overhead low, this predication is only based on an estimation of the target’s present moving speed and direction.
Assume that the target’s present location in OLi is (xi, yi) at time ti and (xi-1, yi-1) in previous location OLi-1 at time ti-1. Then, the target’s speed can be estimated as
![]() (2)
(2)
while the direction is given by
![]() (3)
(3)
Based on this information, the predicted location for the target (xi+1, yi+1) after a given time t is given by
![]() (4)
(4)
To be more precise, it can be shown that the target’s next location obeys a two-dimensional Gaussian distribution with (xi+1, yi+1) as the method.
The accuracy of the “prediction” is very important if the beacon is identified accurately and the overall tracking protocol is effective. While many prediction mechanisms are possible, what was chosen is a linear predictor, which only uses the previous two locations to linearly predict the third location. Higher order prediction is also adopted, which predicts the nth location information based on previous (n-1)th actual locations. Higher order prediction results in more accurate results, though, at the cost of greater energy consumption.
(5) Beacon election process. When current node bi gets an initial estimation of the target state from previous step, it will determine the next best sensor ci and the immediate sensor of ci for tracking among all its neighbors in the face and hand off the state of target information to ci. When a sensor ci detects target o, it becomes active and ci does a comparison of its own target timestamp with the immediate neighbor’s target timestamp. For example, node υ1 sends a detect message to node υ7. After receiving the message, b7 compares with sensor b6. If b7 is close to the target in the face, it will become a beacon.
If two nodes are at the same distance from the target i.e., the same timestamp, then the node with the lower ID number will become the beacon node. Node bi sends a message to tracker T about the new node ci and ci changes its state to be active. Node ci computes the new estimation for the possible future beacon.
The main assumption made by this PET is that each node in the network can locally estimate the cost of sensing, processing, and communicating data to another node. Each node does not need to be active if it is not close to the target. In this process one node is in the active state most of time and at most two nodes cooperate with the active node for a period of time. Sensor network does not need to use more than two nodes at the same time and can monitor power usage.
5 Simulation studies and analyses
In order to evaluate the performance of the PET protocol via simulations, the OMNet++ software and the Mobility Framework fw2.0p3 (http://mobility-fw. sourceforge.net/) were used. The version of the OMNet++ is 3.32. The PET protocol was implemented on stationary nodes and mobile target. In the simulations this proposed protocol was compared with DOT [16] and a flooding-based target tracking protocol. DOT protocol has better performance than the flooding-based target tracking protocols. There are three kinds of target tracking protocols, namely, threshold flooding (TF), schedule flooding, and schedule updating based on flooding. This proposed protocol is compared with DOT and TF.
In DOT and TF protocols, target discovery process is similar. When the tracker obtains the location of moving target, it will move towards the obtained location and carry out the target discovery process repetitively, but PET protocol has no repetition of the target discovery process except in the special case of target missing. In DOT, a mobile target may move in any way, so all the ways the sensors need to be active, then it consumes energy and incurs wakeup delay, which can lead to long message delay in which a large volume of messages is exchanged. The PET improves all these situations. Table 1 shows the parameters and values used in OMNet++ simulations.
Table 1 Simulation parameters and their values

5.1 Simulation metrics
Four metrics were considered for this proposed protocol performance evaluation: (1) missing rate that is the ratio of the number of missed reports to the sensing range, (2) the first capturing time, (3) prediction error, and (4) average energy consumption that is energy consumed both in active and sleeping modes by the network during the simulated period.
5.2 Simulation results
In order to observe the accuracy of this tracking process, the missing rate was investigated. As shown in Fig.6, this protocol offers a smaller missing rate compared with DOT protocol since the moving pattern of the mobile target is random. We consider the sensing range up to 20 m, while communication range is 40 m. We set the values at 5, 10, 15 and 20 m. When the sensing range is the minimum, the maximum missing rate is shown. When the sensing range is set at 5 m, the missing range is about 29% in PET, 38% in DOT and 68% in TF. When the sensing range is 20 m, the missing range is about 13% in PET, 16% in DOT and 19% in TF. These show that if the sensing range is large, the very low missing rate is achieved. Due to the inaccurate prediction of location, very few nodes miss the target but the real location of the target is in the sensing range of face neighbor.

Fig.6 Average missing rate estimated by total missing rate happened in different experimental periods based on sensing range of target tracking sensor
Fig.7 shows first target capturing time in PET. In each simulation run, the target speed is changed. Both tracker and target speeds are set from 5 to 20 m/s. Fig.7 shows that when target speed is 5 m/s, it takes about 88 s in PET, 138 s in DOT and 231 s in TF to capture the target. When the target speed is the maximum of 20 m/s, it takes about 43 s in PET, 58 s in DOT and 126 s in TF to capture the target. It is seen in the figure that when the tracker’s velocity is fast, it can capture the target in a short time. This is because the tracker does not need to often use the flooding, and to adjust face tracks.
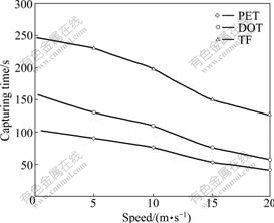
Fig.7 Performance comparison among three protocols at the time when target is captured first time
Fig.8 depicts the prediction error in the PET. The prediction error is presented for up to 300 s. It can be seen that some prediction error points are 22 m at time (54 s, 55 s), 27 m at time (178 s, 179 s), 43 m at time (185 s, 186 s) and 18 m at time (243 s, 244 s). With the prediction error, the active tracking node may fail to detect the target’s position. In the PET, the active node then cooperates with the immediate neighbors.

Fig.8 Average prediction error calculated by distance (di) between actual position of target and predicted primary node
In order to analyze the energy consumption, there was an observation on the difference between this protocol and others as shown in Fig.9. Each experiment was run for 1 500 s. The energy consumption is averaged out by the data gathered from 30 uninterrupted experiments. Fig.9 illustrates the average energy consumption when the target is captured. The target velocity is changed from 5 to 20 m/s. When the target velocity is between 15 and 20 m/s, energy consumption of PET is drastically reduced, while those of DOT and TF do not change obviously.

Fig.9 Average energy consumption when target is caught in different simulation experiments
6 Conclusions
(1) A novel energy efficient target tracking protocol is proposed using sensor networks for tracking the movement of a target such as people or vehicles in open outdoor environments. One important thing is that the target velocity and direction are not constant in this protocol. Target moving in different directions and at different speeds were considered. The result shows that using sensor information fusion in cooperation can greatly improve the accuracy of tracking.
(2) Comparing the simulation results and data with those of the DOT protocol and a flooding based protocol, this proposed protocol greatly contributes to energy conservation by simplifying sensor’s calculation, and minimizing the volumes of message exchanged between sensors as well as sensors and tracker. The number of packet overhead is gradually increased in the PET compared with that in the DOT while the tracker velocity increases.
(3) It is mentionable that both analytically and practically investigations were carried out to track the target in a populated sensor network. The investigation gives a confirmative answer and challenges the long-held paradigm that high tracking quality necessitates high power consumption, but the power consumption can be lessened by reducing the number of nodes involved in target tracking.
References
[1] WANG Q X, CHEN W P, ZHENG R, KIHWAL L, SHA L. Acoustic target tracking using tiny wireless sensor devices [C]// Proceedings of the 2nd International Workshop on Information Processing in Sensor Networks. Berlin: Springer Press, 2003: 642-657.
[2] LIN C Y, TSENG Y C. Structures for in-network moving object tracking in wireless sensor networks [C]// Proceedings of the First International Conference on Broadband Networks. Washington DC: IEEE Press, 2004: 718-727.
[3] XU Y Q, WINTER J, LEE W C. Prediction-based strategies for energy saving in object tracking sensor networks [C]// Proceedings of the 2004 IEEE International Conference on Mobile Data Management. Berkeley, California: IEEE Press, 2004: 346-357.
[4] JAEHOON J, TAEHYUN H, TIAN H, DAVID D. MCTA: target tracking algorithm based on minimal contour in wireless sensor networks [C]// Proceedings of the 26th IEEE International Conference on Computer Communications. Alaska, USA: IEEE Press, 2007: 2371-2375.
[5] XING Xiao-fei, WANG Guo-jun, WU Jie. Herd-based target tracking protocol in wireless sensor networks [C]// Proceedings of the International Conference on Wireless Algorithms, Systems and Applications (WASA 2009). Boston: August 2009.
[6] BHUIYAN M Z A, WANG G J, WU J. Target tracking with monitor and backup sensors in wireless sensor networks [C]// Proceedings of the 18th IEEE International Conference on Computer Communications and Networks (ICCCN 2009), San Francisco, 2009.
[7] SAMIR G, TOMASZ I. Prediction-based monitoring in sensor networks: Taking lessons from MPEG [C]// Proceedings of the Computer Communication Review. New York: ACM, 2001, 31(5): 82-98.
[8] WANG Xue, MA Jun-jie, WANG Sheng, BI Dao-wei. Prediction- based dynamic energy management in wireless sensor networks [J]. Sensors Journal, 2007, 7: 251-266.
[9] XU Y Q, LEE W C. On localized prediction for power efficient object tracking in sensor networks [C]// Proceedings of the 23rd International Conference on Distributed Computers Systems Workshops. Washington DC: IEEE Computer Society Press, 2003: 434-439.
[10] TSENG Y C, KUO S P, LEE H W, HUANG C F. Location tracking in a wireless sensor network by mobile agents and its data fusion strategies [C]// Proceedings of International workshop on Information Processing in Sensor Networks. Berlin: Springer Press, 2003: 625-641.
[11] XU Ying-yue, QI Hai-rong. Mobile agent migration modeling and design for target tracking in wireless sensor networks [J]. ScienceDirect Journal on Ad Hoc Networks, 2008, 6: 1-16.
[12] CHEN Ying-wen, XU Ming, WU Yi. Optimization of the proxy node selection for in-network data processing in wireless sensor networks [J]. Journal of Software, 2007, 18(12): 3104-311. (in Chinese)
[13] HUANG Q F, LU C Y, ROMAN G C. Reliable mobicast via face-aware routing [C]// Proceedings of the 23rd Annual Joint Conference of the IEEE Computer and Communications Societies. CA: IEEE Computer Society Press, 2004: 2108-2118.
[14] HUANG Q F, SANGEETA B, LU C Y, ROMAN G C. FAR: Face-aware routing for mobicast in large-scale sensor networks [J]. ACM Transactions on Sensor Networks, 2005, 1: 240-271.
[15] GUO M, OLULE E, WANG G, GUO S. Designing energy efficient target tracking protocol with quality monitoring in wireless sensor networks [J]. The Journal of Supercomputing, 2010, 51(2): 131-148.
[16] TSAI H W, CHU C P, CHEN T S. Mobile object tracking in wireless sensor networks [J]. Computer communications, 2007, 30(8): 1811- 1825.
[17] KIRILL M, SAMEER S, YOUNGMIN K, GUL A. Cooperative tracking with binary-detection sensor networks [C]// Proceedings of the 1st International Conference on Embedded Networked Sensor Systems. New York: ACM, 2003: 332-333.
[18] RAJEEV S, ANANDA A, MUN C C, WEI Tsang-ooi. Mobile, Wireless, and sensor networks: Technology, applications, and future directions [M]. New Jersey: Wiley-IEEE Press, 2006: 179-189.
[19] CHU Hung-chi, JAN Rong-hong. A GPS-less self-positioning method for sensor networks [C]// Proceedings of the 11th International Conference on Parallel and Distributed Systems. Washington DC: IEEE Computer Society, 2005: 629-633.
[20] FURNAS W J. Two dimensional magnetic field sensor [C]// Proceedings of the 1990 IEEE Southern Tier Technical Conference. New York: IEEE Press, 1990, 7990: 225-232.
[21] SRINIVASAN A, WU J. A survey on secure localization in wireless sensor networks. Encyclopedia of wireless and mobile communications [C]// Taylor and Francis Group. London: CRC Press, 2008.
[22] KIM Y J, RAMESH G, BRAD K, SCOTT S. Geographic routing made practical [C]// Proceedings of the 2nd conference on Symposium on Networked Systems Design & Implementation. Berkeley: USENIX Association, 2005, 2: 217-230.
[23] BEN L, SAYAN M, BARBARA L. Path vector face routing: Geographic routing with local face information [C]// Proceedings of the 13th IEEE International Conference on Network Protocols. Boston: IEEE Press, 2005: 147-158.
[24] LIU Cong, WU Jie. Virtual-force-based geometric routing protocol in MANETs [J]. IEEE Transactions on Parallel and Distributed Systems, 2009, 20(4): 433-445.
Foundation item: Project(07JJ1010) supported by the Hunan Provincial Natural Science Foundation, China; Project(NCET-06-0686) supported by Program for New Century Excellent Talents in University; Project(IRT0661) supported by Program for Changjiang Scholars and Innovative Research Team in University
Received date: 2009-05-03; Accepted date: 2009-09-19
Corresponding author: WANG Guo-jun, PhD, Professor; Tel: +86-731-88877711; E-mail: csgjwang@mail.csu.edu.cn
(Edited by LIU Hua-sen)

